Hospitals and outpatient clinics are increasingly choosing to build telehealth platform solutions in response to direct operational and financial pressure. Workforce shortages, a growing chronic patient population, overloaded outpatient facilities, and rising expectations for faster access to care are making the traditional in-person model increasingly inefficient.
This shift is visible at the macro level: 77% of countries in the WHO European Region use telemedicine services, and 84% have implemented teleradiology, signaling a systemic move toward remote care delivery.
Market dynamics further reinforce this trend. The global telehealth market, valued at $49.9 billion in 2019, is projected to reach $459.8 billion by 2030. The pandemic acted as a catalyst, driving telehealth visits from 14 million in 2019 to approximately 200 million by 2021. While volumes declined after the peak, by 2025, telehealth had stabilized as a permanent care channel rather than a temporary crisis response.
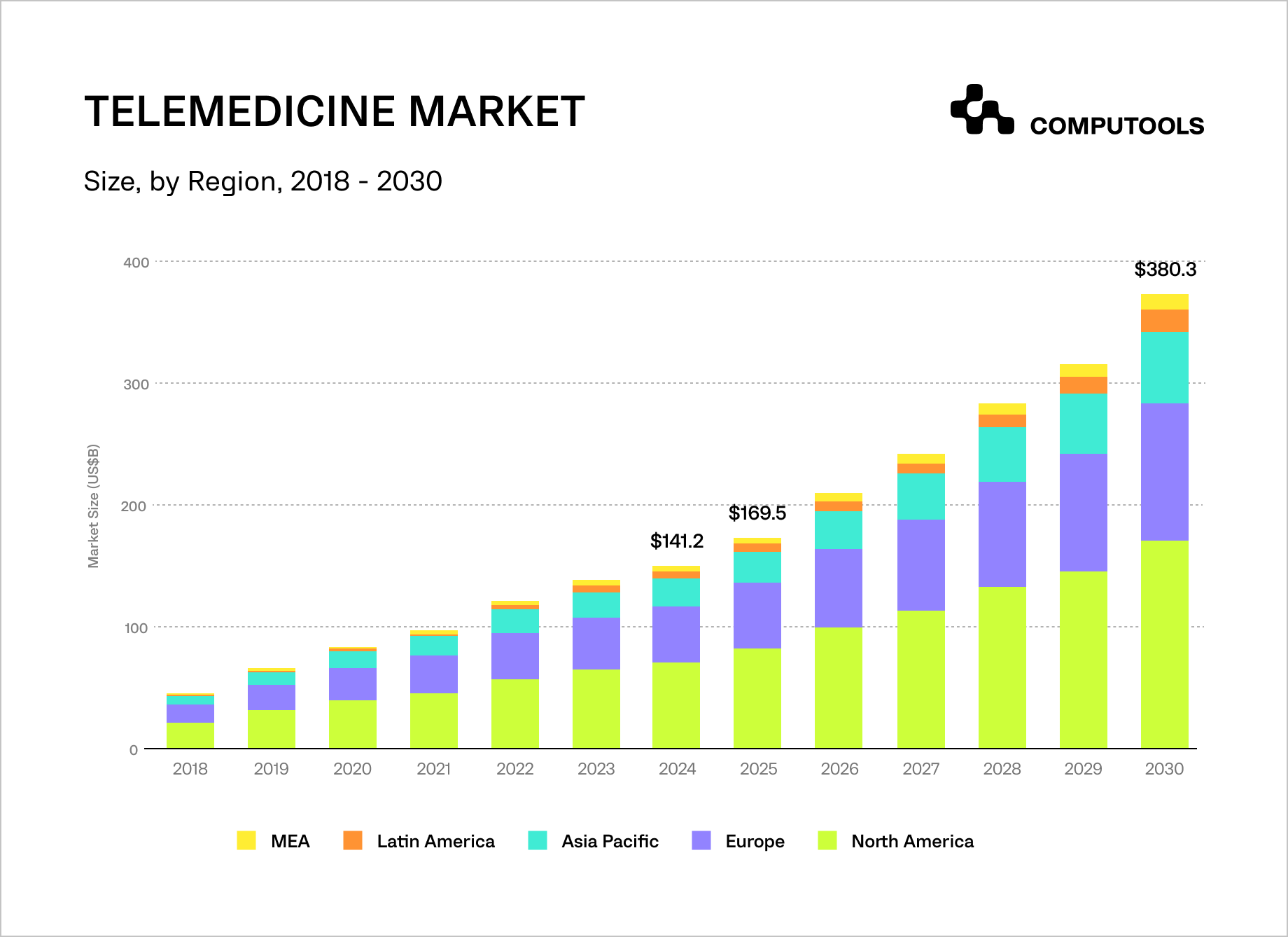
For most healthcare organizations, the main challenge is executing them effectively. Fragmented implementations—standalone video tools, disconnected scheduling, and limited integration with EHR, billing, and insurance systems—often increase costs rather than reduce them.
According to WHO, funding remains the primary barrier to scaling telehealth, followed by infrastructure limitations and insufficient digital skills among staff. This is why hospitals increasingly seek comprehensive telemedicine software for clinics rather than isolated features.
How we built a scalable hospital software platform for Safety Healthcare
For Safety Healthcare, a provider of high-tech patient safety solutions, we were engaged to solve a critical operational challenge: the lack of real-time visibility and control over medical equipment across healthcare facilities. While not a telehealth product itself, the platform addressed the same systemic issues hospitals face when they decide to build telehealth platform solutions—fragmented data, manual workflows, and limited operational transparency that directly affect care delivery, staff efficiency, and financial performance.
Our team delivered the solution end-to-end as part of our hospital software development services, designing and implementing a secure, cloud-ready application for real-time tracking of medical equipment using RFID tags and barcodes. We integrated authentication services, help desk workflows, notifications, and advanced search capabilities, ensuring the system could operate reliably across web and mobile environments.
Particular attention was given to data security, role-based access, and system resilience—core requirements for any healthcare platform functioning in regulated clinical settings.
From an architectural perspective, the solution was built using a scalable telehealth platform architecture mindset: modular services, clear integration boundaries, and the ability to evolve without disrupting live hospital operations.
This approach enabled rapid iteration, simplified testing across multiple hospital environments, and ensured the platform could scale as operational complexity increased.

The impact was measurable. Safety Healthcare achieved a 56% increase in revenue and a 74% reduction in checkout time while improving patient safety and streamlining internal workflows.
This case demonstrates our ability to deliver production-grade healthcare platforms and also our broader expertise in building scalable, secure digital health solutions. Drawing on this experience and similar projects beyond this case, we now break down, step by step, how to build a telehealth platform for hospitals and outpatient clinics.
Full guide: how to build a telehealth platform for hospitals and outpatient clinics
Step 1. Define Clinical Scope, Use Cases, and Care Delivery Model
Successful telehealth platform development starts with clearly defining what type of care is being delivered, to whom, and under which clinical and operational constraints. Hospitals and outpatient clinics operate under fundamentally different conditions, and treating telehealth as a generic “video consultation tool” is the most common reason platforms fail to scale or deliver ROI.
At this stage, the goal is to translate clinical reality into explicit, documented use cases. This includes identifying which interactions can safely and effectively move to virtual care (e.g., follow-up visits, chronic disease check-ins, triage, post-discharge monitoring) and which must remain in-person. Telehealth should build on current care models without disrupting clinical responsibility or fragmenting patient journeys.
Equally important is defining user roles and responsibilities. A hospital-grade telehealth platform must support multiple actors beyond doctors and patients: nurses, care coordinators, administrators, and technical support staff. Each role has different access levels, workflows, and compliance requirements. Failing to define these upfront leads to security gaps, inefficient interfaces, and role conflicts later in development.
Operational workflows must be mapped before any feature decisions are made. This includes appointment scheduling logic, intake and pre-visit data collection, escalation paths, documentation handoff to EHRs, and post-visit follow-ups. In hospital environments, telehealth workflows must coexist with existing systems and policies rather than operate in parallel.
This approach mirrors how we worked with Safety Healthcare. Before implementing any technical solution, we analyzed how hospitals actually manage critical assets, where delays occurred, and how fragmented tools increased operational risk.
That same discipline, starting with real workflows rather than assumed features, is essential when defining the scope of a telehealth platform intended for clinical use.
By the end of Step 1, stakeholders should have:
• a validated list of clinical use cases suitable for telehealth,
• clearly defined user roles and responsibilities,
• documented workflows that integrate with existing hospital or clinic operations,
• and a shared understanding of what success looks like from both clinical and operational perspectives.
Only after this foundation is in place does it make sense to move on to architectural and feature-level decisions.
Step 2: Define Your Telehealth Platform Strategy: Buy, Build, or Hybrid
Once clinical scope and workflows are clearly defined, hospitals and outpatient clinics face a critical strategic decision: adopt an off-the-shelf telemedicine product or invest in custom telehealth software development. This choice directly affects scalability, compliance, long-term costs, and the ability to integrate telehealth into core clinical operations.
Off-the-shelf telemedicine tools are often attractive for quick pilots or limited use cases. They typically offer video calls, basic scheduling, and messaging with minimal setup. However, these solutions are designed for broad applicability rather than deep integration into hospital-grade environments.
As a result, they frequently create operational silos—separate logins, duplicate data entry, disconnected billing, and manual handoffs between systems. For hospitals and multi-site outpatient networks, these limitations become structural risks.
Lack of control over data models, restricted integration with EHRs, inflexible workflows, and vendor-dependent roadmaps make it difficult to adapt telehealth to evolving clinical, regulatory, or reimbursement requirements. Over time, license costs combined with operational inefficiencies often exceed the initial savings of “buying fast.”
A custom platform strategy emphasizes control, interoperability, and scalability. Instead of modifying clinical processes for a generic product, it aligns with existing care models, policies, and regulations. This is vital for organizations across multiple departments, locations, or care types.
The Safety Healthcare case reflects this logic. Rather than deploying disconnected tracking tools, the solution was built as a unified platform aligned with hospital workflows, security requirements, and operational objectives. That architectural discipline enabled measurable improvements in efficiency and revenue without introducing parallel systems or manual workarounds. The same principle applies to telehealth platforms intended for real clinical use.
At this stage, decision-makers should evaluate:
• depth of required EHR, billing, and identity management integration,
• ability to customize workflows without vendor constraints,
• data ownership and auditability,
• scalability across departments and locations,
• and the total cost of ownership over a multi-year horizon.
In most hospital and outpatient clinic contexts, telehealth is a capability embedded into the broader digital health ecosystem. When telehealth is expected to support core care delivery, reporting, and compliance—not just video visits—a custom platform strategy becomes a structural advantage rather than a technical preference.
Step 3: Design the Architecture and Integration Blueprint
Designing a telemedicine platform for hospitals starts with architecture. Hospital environments are inherently complex: multiple departments, parallel clinical workflows, strict security requirements, and deep dependence on legacy systems. A telehealth platform that is not architected for this complexity will quickly become a bottleneck instead of an enabler.
The primary architectural goal is interoperability. Telehealth must function as an extension of the hospital’s existing digital landscape, integrating with EHR systems, identity and access management, billing, scheduling, and reporting tools. This requires clearly defined integration boundaries, standardized data exchange (FHIR/HL7 where applicable), and role-based access control embedded at the platform level.
Hospitals gain advantages from adopting modular system architectures. Key services, like authentication, patient identity, scheduling, communication, and audit logs, should be isolated from clinical logic and UI layers. This separation enables hospitals to update or expand specific components, such as introducing new care pathways or integrating more departments, without risking the stability of the whole system.
Security and compliance must be foundational. Hospitals operate under continuous audit pressure, so the architecture must support encryption at rest and in transit, detailed access logs, consent management, and traceability of all clinical interactions. These requirements influence technology choices, infrastructure setup, and even API design from the very beginning.
Operational resilience is another key architectural concern. Telehealth platforms must remain available during peak loads, staff shortages, or emergency situations. This means designing for horizontal scalability, fault tolerance, and controlled degradation, ensuring that critical workflows continue even if non-essential components fail.
Our work with Safety Healthcare demonstrates the value of this approach. The platform was designed to integrate authentication services, notification systems, search infrastructure, and secure data access into a single operational backbone. That architectural consistency enabled hospitals to manage real-time processes reliably without introducing additional system fragmentation, an outcome equally critical for telehealth platforms operating in hospital settings.
By the end of Step 3, hospitals should have:
• a high-level system architecture aligned with clinical and operational complexity,
• defined integration points with core hospital systems,
• a security and compliance model embedded into the platform design,
• and an architecture capable of scaling across departments and care models.
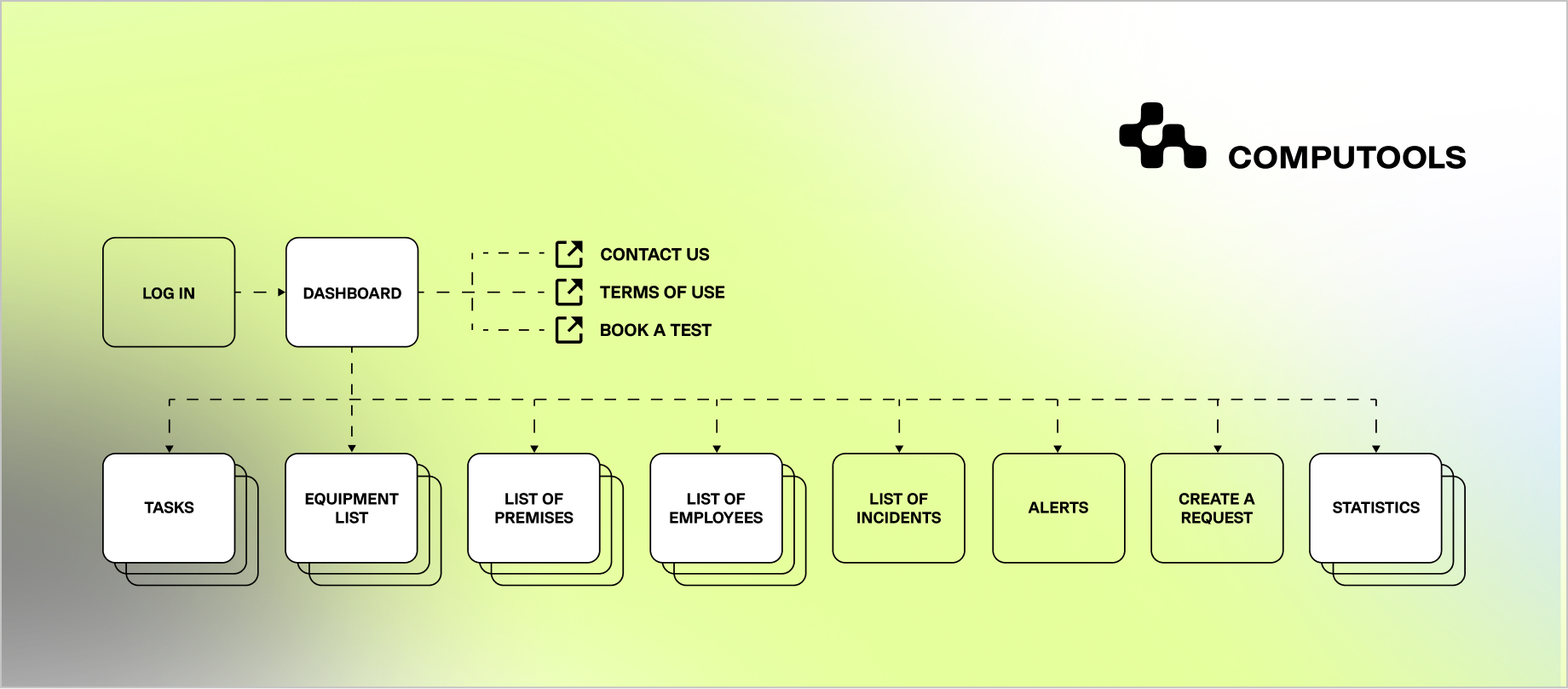
Step 4. Adapt the Platform for Outpatient Clinics and Ambulatory Care Workflows
While hospitals require deep system integration and high operational resilience, outpatient clinics and ambulatory care centers prioritize speed, usability, and cost efficiency. Telehealth solutions for outpatient clinics must reduce administrative load, increase patient throughput, and fit into lean clinical teams without introducing technical or process overhead.
The core difference lies in workflow design. Outpatient clinics typically operate with shorter visits, higher patient turnover, and limited on-site IT support. Telehealth must simplify intake, scheduling, and follow-ups rather than replicate hospital-grade complexity. This means minimizing clicks, automating routine tasks, and surfacing only clinically relevant data at the point of care.
Platform configuration should allow clinics to customize care pathways without code changes. For example, specialty-specific questionnaires, appointment templates, and follow-up protocols should be configurable through admin tools. Clinics need flexibility to adapt telehealth workflows to dermatology, mental health, primary care, or post-operative check-ins without rebuilding the platform.
Integration priorities also differ. While hospitals focus on deep EHR interoperability, outpatient clinics often need lightweight integrations with practice management systems, billing providers, and notification services. Telehealth platforms must support both scenarios without branching into separate products. A unified core with configurable modules ensures consistency across care settings.
Automation plays a critical role in outpatient environments. Appointment reminders, pre-visit forms, prescription renewals, and post-visit instructions should be automated to reduce staff workload. This directly impacts financial performance by lowering no-show rates, shortening visit cycles, and freeing clinicians to focus on care rather than administration.
The Safety Healthcare project reinforces this principle. Although the platform addressed hospital-grade operational needs, its success came from simplifying day-to-day workflows through intuitive interfaces, fast search, and real-time notifications. The same design philosophy applies to outpatient telehealth: complexity belongs in the system architecture, not in the user experience.
By the end of Step 4, organizations should have:
• outpatient-specific telehealth workflows aligned with clinic operations,
• configurable care pathways without engineering dependency,
• automation mechanisms that reduce administrative burden,
• and a platform that scales consistently across hospitals and clinics without fragmentation.
Step 5. Define Core Telemedicine Platform Features Based on Clinical and Operational Value
At this stage, healthcare telehealth app development shifts from architecture and workflows to feature definition driven by real clinical and operational value, not by generic product checklists. The objective is to support end-to-end care delivery—before, during, and after a virtual encounter—while minimizing friction for both clinicians and patients.
Core telemedicine platform features should be mapped directly to the workflows defined in earlier steps. For patients, this includes secure onboarding, appointment management, structured pre-visit questionnaires, video or audio consultations, access to medical records, prescriptions, and post-visit instructions. Each feature must reduce uncertainty, shorten time to care, and improve continuity rather than simply replicate in-person interactions digitally.
For clinicians, features must support efficiency and decision-making under time pressure. This includes role-based dashboards, quick access to patient history, structured documentation, scheduling visibility, and secure messaging. The platform should reduce cognitive load by surfacing relevant data at the right moment, not by overwhelming providers with unnecessary screens or options.
Administrative and operational features are equally critical. Clinics and hospitals require tools to manage users and roles, configure care pathways, monitor platform usage, and generate audit-ready reports. These capabilities enable governance, compliance, and continuous optimization without relying on engineering intervention for routine changes.
Security and compliance are embedded characteristics across all functionality. Consent management, access logging, encryption, and data retention rules must be applied consistently across video calls, messaging, file sharing, and analytics. Feature design must assume regulatory scrutiny and clinical accountability from day one.
The Safety Healthcare case demonstrates how feature selection tied to operational needs drives measurable outcomes. Real-time tracking, fast search, notifications, and secure access were not added for completeness; they directly reduced delays, improved staff efficiency, and delivered quantifiable business impact. Telehealth platforms require the same discipline: features exist to solve operational problems, not to decorate the product.
By the end of Step 5, organizations should have:
• a prioritized feature set aligned with clinical and operational workflows,
• clear separation of patient, clinician, and admin capabilities,
• built-in compliance and security across all interactions,
• and a feature roadmap that supports phased rollout without rework.
Step 6. Automate Telehealth Workflows to Reduce Clinical and Administrative Load
Once core features are defined, the real scalability of a telehealth platform is achieved through telehealth workflow automation. Without automation, telehealth simply shifts work from physical rooms to digital interfaces while preserving the same inefficiencies, manual handoffs, and staffing constraints.
Workflow automation should focus on removing repetitive, low-value tasks from clinical and administrative staff. This starts before the visit, with automated appointment confirmations, reminders, eligibility checks, and structured pre-visit questionnaires that collect symptoms, history, and consent in advance. By the time a clinician joins a session, the relevant context is already available.
During care delivery, automation supports routing and prioritization. Incoming appointment requests can be triaged based on specialty, urgency, or availability rules. Follow-ups, referrals, and prescription renewals can be triggered automatically based on visit outcomes, reducing delays and preventing missed actions. In outpatient settings, this directly improves throughput; in hospitals, it reduces coordination overhead across departments.
Post-visit automation is equally important. Discharge instructions, care plans, prescriptions, and follow-up appointments should be generated and delivered automatically, while visit summaries are stored and synchronized with EHR systems. Automated notifications ensure that both patients and care teams stay aligned without manual outreach.
From an operational perspective, automation enables monitoring and optimization. Platform administrators can track no-show rates, visit durations, clinician utilization, and patient engagement without manual reporting. These insights allow healthcare organizations to continuously adjust staffing, scheduling, and care models based on real usage data.
The Safety Healthcare platform followed the same principle. Automated notifications, integrated search, and streamlined data access reduced operational friction and shortened process cycles. Applying automation at the platform level rather than relying on staff vigilance was key to achieving sustainable efficiency gains. Telehealth platforms benefit from the same approach when automation is treated as core infrastructure rather than an optional add-on.
By the end of Step 6, organizations should have:
• automated pre-visit, visit, and post-visit workflows,
• reduced dependency on manual coordination and reminders,
• operational visibility through real-time metrics,
• and a telehealth platform capable of scaling care delivery without proportional staffing increases.
Even with automated workflows, clinical documentation often remains manual — this guide explains how to integrate AI-based charting systems into hospital telehealth without increasing compliance risk.
Step 7. Ensure Regulatory Readiness and Operational Stability
At this stage, the telehealth platform must move from implementation to operational maturity. Building features and workflows is not sufficient if the system cannot consistently meet regulatory, security, and audit requirements in real clinical use.
A HIPAA compliant telehealth platform is defined not by documentation alone, but by how data, access, and accountability are enforced in everyday operations.
Compliance must be embedded across the platform lifecycle. This includes role-based access control, encrypted communication and storage, audit logs for all clinical interactions, and clear data retention policies. These mechanisms ensure traceability and protect healthcare organizations from regulatory exposure while maintaining patient trust.
Operational stability is equally critical. Telehealth platforms must remain reliable during peak usage, staffing shortages, or emergency scenarios. This requires proactive monitoring, incident response procedures, and the ability to deploy updates without disrupting active care delivery. Compliance without reliability creates operational risk; reliability without compliance creates legal risk.
The Safety Healthcare platform followed the same principle. Security controls, system monitoring, and controlled integrations were treated as core infrastructure, not post-launch additions. This approach enabled continuous use in regulated healthcare environments without compromising safety or performance.
By the end of Step 7, organizations should have:
• enforceable security and access controls across the platform,
• continuous monitoring and audit readiness,
• operational processes aligned with regulatory expectations,
• and confidence that telehealth can function as a permanent care channel, not a temporary solution.
Delivering and scaling telehealth platforms in production environments requires healthtech software development services with experience in regulated healthcare systems, operational workflows, and long-term support models.
Step 8. Scale, Measure Outcomes, and Evolve the Telehealth Platform
Once the telehealth platform is stable, compliant, and operational, the final step is turning it into a long-term care delivery capability rather than a fixed product. This requires continuous measurement, controlled scaling, and deliberate platform evolution based on real clinical and operational data.
Scaling should follow validated usage patterns. Healthcare organizations must monitor core metrics, including visit completion rates, no-show reduction, clinician utilization, patient satisfaction, and downstream clinical outcomes. These indicators reveal where telehealth delivers value and where workflows or features need adjustment. Scaling without this feedback loop risks amplifying inefficiencies instead of benefits.
Platform evolution increasingly depends on extending care beyond episodic virtual visits. This is where remote patient monitoring integration becomes strategically important. By incorporating connected devices and wearables, telehealth platforms enable continuous monitoring of chronic conditions, post-discharge recovery, and care for high-risk patients. This shifts telehealth from reactive consultations to proactive, preventive care models.
Operationally, this evolution must remain controlled. New capabilities should be introduced through modular expansion rather than disruptive redesigns. Governance processes, covering data usage, access rights, clinical responsibility, and regulatory alignment, must evolve alongside functionality to preserve trust and compliance as the platform grows.
The Safety Healthcare project demonstrates the value of this mindset. The solution did not stop at initial deployment; it was designed for ongoing optimization, monitoring, and improvement as operational needs evolved. Telehealth platforms require the same long-term perspective to remain relevant in dynamic healthcare environments.
By the end of Step 8, organizations achieve the following:
• data-driven scaling based on real usage and outcomes,
• extension from episodic care to continuous monitoring,
• controlled platform evolution without operational disruption,
• and a telehealth system positioned as a permanent component of digital healthcare delivery.
Following these steps allows healthcare organizations to build a telehealth platform that is clinically aligned, operationally scalable, and ready for long-term use across hospitals and outpatient clinics.

Translate telehealth strategy into a HIPAA-ready, scalable platform. Request a technical and cost assessment tailored to hospital and outpatient environments.
What makes a telehealth platform scalable in clinical practice
When healthcare organizations build telehealth platform solutions for real clinical environments, success depends on prioritizing capabilities that deliver measurable clinical and operational value.
Core capabilities to prioritize:
• Clinical-grade video consultations. Video must function as a full clinical workflow, including patient–provider routing, pre-visit context, consent, documentation, and reliable connectivity with encryption and adaptive bandwidth handling.
• Intelligent appointment scheduling. Scheduling logic should automatically manage provider availability, visit types, time zones, and follow-ups, with admin controls for exceptions such as cancellations and overbooking.
• EHR integration and data integrity. Telehealth platforms must support secure, bidirectional data exchange with electronic health records, enforce role-based access, maintain audit trails, and ensure compliant data handling from day one.
• Prescription and treatment workflows. Structured prescribing, eRx integration, approval flows, and refill management should be embedded into the care journey, with clear traceability for compliance.
• Payments and billing transparency. The platform should support flexible pricing models—cash pay, subscriptions, and bundled services — while providing clear receipts, reconciliation, and reporting for finance teams.
• Analytics and performance visibility. Role-based dashboards should expose operational KPIs, provider utilization, patient engagement, and outcome trends to support continuous optimization.
• AI-enabled operational support. Practical AI use cases include symptom intake, visit documentation, no-show prediction, risk flagging, and patient support automation, always with clinician oversight and explainability.
This approach reflects custom telehealth platform development for healthcare providers focused on long-term scalability, compliance, and operational efficiency rather than short-term digital experiments.
Why telehealth platforms fail to scale in clinical environments
Most telehealth initiatives fail due to early architectural and operational mistakes. Teams that approach telehealth as a feature set rather than a system often underestimate the complexity of clinical environments.
• The most common failure mode is treating telehealth as a standalone product. When video visits, scheduling, documentation, and billing live outside core systems, clinicians are forced to duplicate work, and operational costs increase rather than decrease. Poor EHR integration exacerbates this problem, turning telehealth into an expensive communication layer rather than a care-delivery channel.
• Another frequent issue is reliance on manual workflows that do not scale. Human coordination for reminders, follow-ups, routing, and reporting may work in pilots but collapses under real patient volume. Similarly, post-launch compliance handling almost always leads to retrofitting security, access control, and audit logic, introducing risk and technical debt.
• Finally, many platforms lack ownership of analytics and outcomes. Without clear accountability for utilization, quality metrics, and financial performance, telehealth becomes invisible to leadership and impossible to optimize. When no one owns the data, no one owns the result.
Regulatory and regional considerations that cannot be ignored
Telehealth platforms operate in heavily regulated environments, and regional requirements directly shape system design. In the United States, teams that aim to build a HIPAA compliant telehealth platform from scratch must embed security, access controls, auditability, and data governance into the architecture from day one. Compliance cannot be achieved through policies alone—it must be enforced technically at every interaction point.
In the European Union, GDPR introduces additional constraints around medical data processing, patient consent, data minimization, and cross-border transfers. These requirements affect storage models, logging, data residency, and even UX decisions inside patient-facing components, including telehealth patient portal development.
Licensing and cross-border care rules further complicate platform design. Provider eligibility, jurisdictional restrictions, and care delivery boundaries must be reflected in scheduling logic and access rules, not managed manually. On top of that, reimbursement models and payer policies differ widely by country and region, influencing how visits are structured, documented, and billed.
Together, these constraints make it clear that telehealth is not a demo-friendly domain. Platforms must be designed for regulatory reality, not abstract use cases; otherwise, scaling becomes legally and operationally impossible.
HIPAA requirements shape the architecture of the healthcare system from the earliest design decisions. The How to Design HIPAA-Compliant HealthTech Architecture From Day One guide focuses on structuring data access, security boundaries, and scalable infrastructure for regulated environments.
Why healthcare organizations choose Computools to build telehealth platform
Healthcare teams work under regulatory pressure, limited staffing, and constant operational load. Software in this environment must remain stable, secure, and usable at scale, not just function in controlled pilot conditions.
Computools has been building healthcare platforms designed for real clinical workflows for over 12 years, with production traffic and long-term operation. Our systems are engineered to handle compliance constraints, data security requirements, and day-to-day clinical volume from the first release.
We deliver end-to-end healthcare software development services for hospitals, outpatient clinics, pharmacies, and healthtech companies from telemedicine platforms and EHR systems to patient engagement solutions, AI-driven clinical tools, and workflow automation.
Every project starts with software architecture development. We design systems to remain interoperable, secure, and maintainable as regulations change, care models evolve, and patient volumes grow. Integration with existing clinical systems is treated as a baseline requirement, not an afterthought.
Our teams provide custom web development aligned with real healthcare workflows. The focus is on clinician usability, system performance, and operational reliability, reducing administrative load, improving care coordination, and supporting measurable efficiency gains.
Cybersecurity and compliance are built into the engineering process from day one. Data protection, access control, audit trails, and regulatory alignment are addressed at the architecture level, ensuring HIPAA- and GDPR-compliant platforms without post-launch retrofitting.
Proven Impact in Healthcare
• 45% faster patient data processing
• 40% reduction in administrative costs
• Up to 30% fewer appointment no-shows
• 25% increase in patient retention
• 20+ HealthTech projects in production environments
• HIPAA, HL7, FHIR, IEC 62304, GDPR compliance expertise
Computools builds healthcare software for real-world delivery where reliability, regulatory compliance, and operational efficiency directly shape clinical outcomes and care continuity. Contact us at info@computools.com to discuss your project.
Not every software team is equipped to work with healthcare constraints. This list, “Top 25 Healthtech Software Development Companies in 2026,” focuses on companies with proven experience in regulated, production healthcare systems.
To sum up
Telehealth delivers value only when it is built as a cost and capacity lever, not as a digital add-on. The economic outcome depends on how well the platform reduces manual coordination, absorbs demand variability, and scales care delivery without proportional growth in staff or overhead.
Organizations that invest in structured architecture, automated workflows, and production-ready execution see predictable business results: lower administrative cost per visit, higher clinician utilization, and sustained service expansion without operational degradation. This is the point where telehealth shifts from innovation spending to a controllable operating asset.
Computools
Software Solutions
Computools is a digital consulting and software development company that delivers innovative solutions to help businesses unlock tomorrow.








“Computools was selected through an RFP process. They were shortlisted and selected from between 5 other suppliers. Computools has worked thoroughly and timely to solve all security issues and launch as agreed. Their expertise is impressive.”