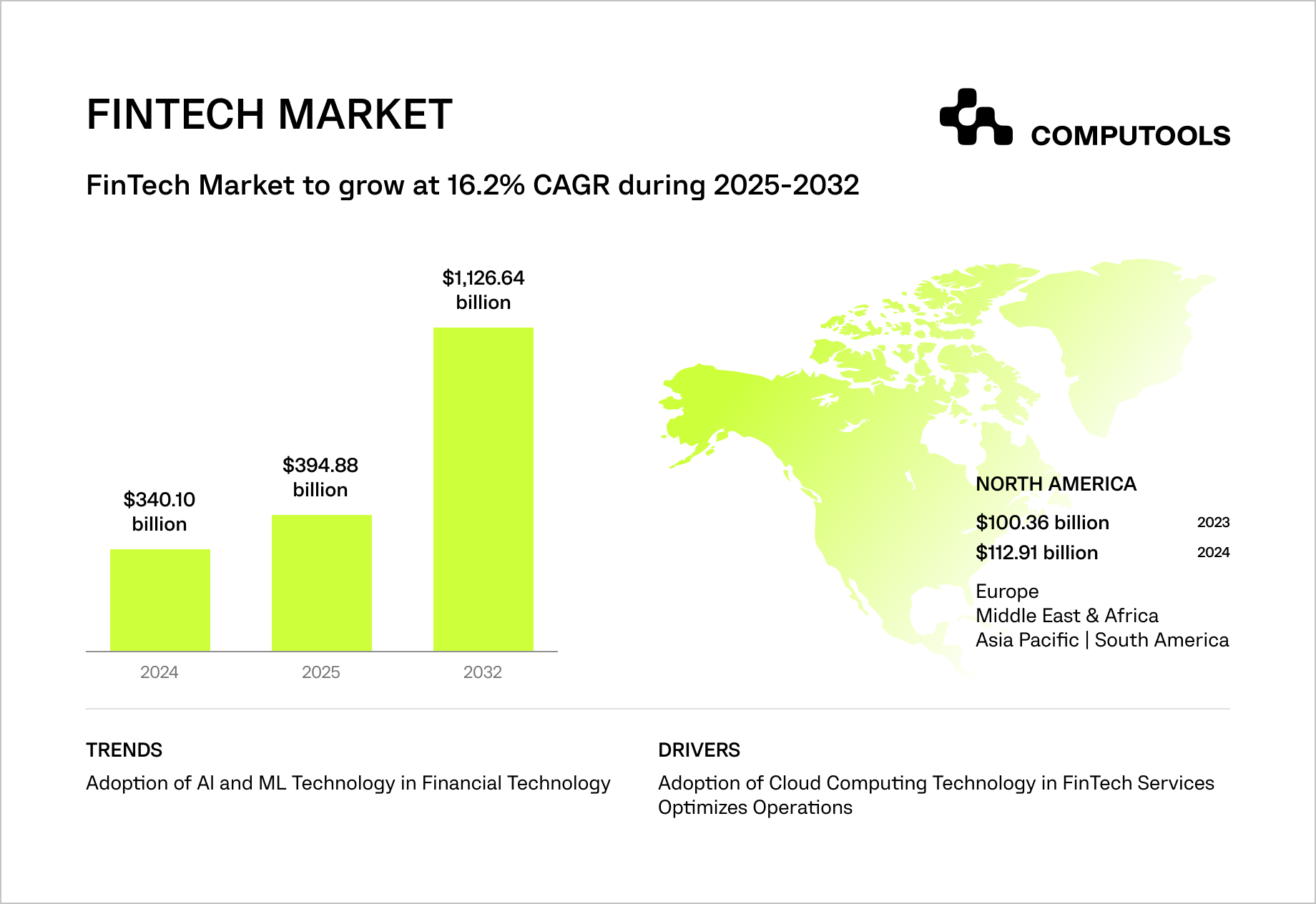
The global fintech market continues to scale at an unprecedented pace. In 2024, it was valued at USD 340.10 billion; it was expected to reach USD 394.88 billion in 2025 and is projected to grow to USD 1,126.64 billion by 2032, reflecting a CAGR of 16.2%.
North America remains the dominant region, accounting for 34.05% of the global market.
The mobile banking market grew from $715.3 million in 2018 to $1,824.7 million by 2026. At the same time, open banking adoption is accelerating, with the global user base projected to surpass 470 million in 2025.
As a result, banking APIs have become a foundational component of most modern fintech mobile apps. In practice, this means that when companies build fintech mobile app solutions, they increasingly rely on complex ecosystems of third-party integrations, including payment gateways, banking APIs, KYC/AML providers, analytics tools, and support services.
Each additional integration expands the attack surface and introduces new security dependencies. In 2024, Ticketmaster experienced a data breach affecting approximately 560 million users, caused by a compromised third-party widget embedded in its checkout flow. The incident illustrates a critical fintech risk: a single weak integration can expose an entire platform.
Compliance is a parallel challenge. To accelerate time-to-market, many fintech teams delay regulatory considerations until after launch. The consequences can be severe.
In 2022, Revolut was fined €3.5 million by Lithuanian regulators for AML violations, including insufficient customer identification and delayed suspicious transaction reports. The core issue was not the lack of compliance rules, but their failure to be integrated into daily operations.
As fintech products scale across users, regions, and integrations, requirements such as GDPR, PCI DSS, and AML/KYC can no longer be treated as external constraints. They must be integral to product design and engineering decisions from the outset.
Secure fintech app architecture is now essential for sustainable growth, not just competitive advantage. We illustrate this by explaining how we built a fintech app with secure banking integrations, using a case study to show architectural choices, integration patterns, and security practices.
How Computools build fintech mobile app solutions in practice: the Moblet case
To move from theory to practice, let’s look at how we build fintech mobile app solutions in a real production environment.
One example is Moblet, a challenger banking platform designed to help businesses and individuals manage finances through precise calculations and secure transactions. The product was conceived as a mobile-first financial management tool that combines account management, expense tracking, investments, and budgeting in a single interface.
From the very beginning, Moblet required more than standard app development. Entering the retail banking segment meant operating in a highly regulated environment while competing with mature fintech products on user experience.
Our focus was on designing an architecture that could support complex calculations, real-time transactions, and multiple banking integrations without exposing sensitive data or creating operational bottlenecks.
This is where our approach to banking software development services came into play—treating security, compliance, and scalability as architectural foundations rather than post-launch enhancements.
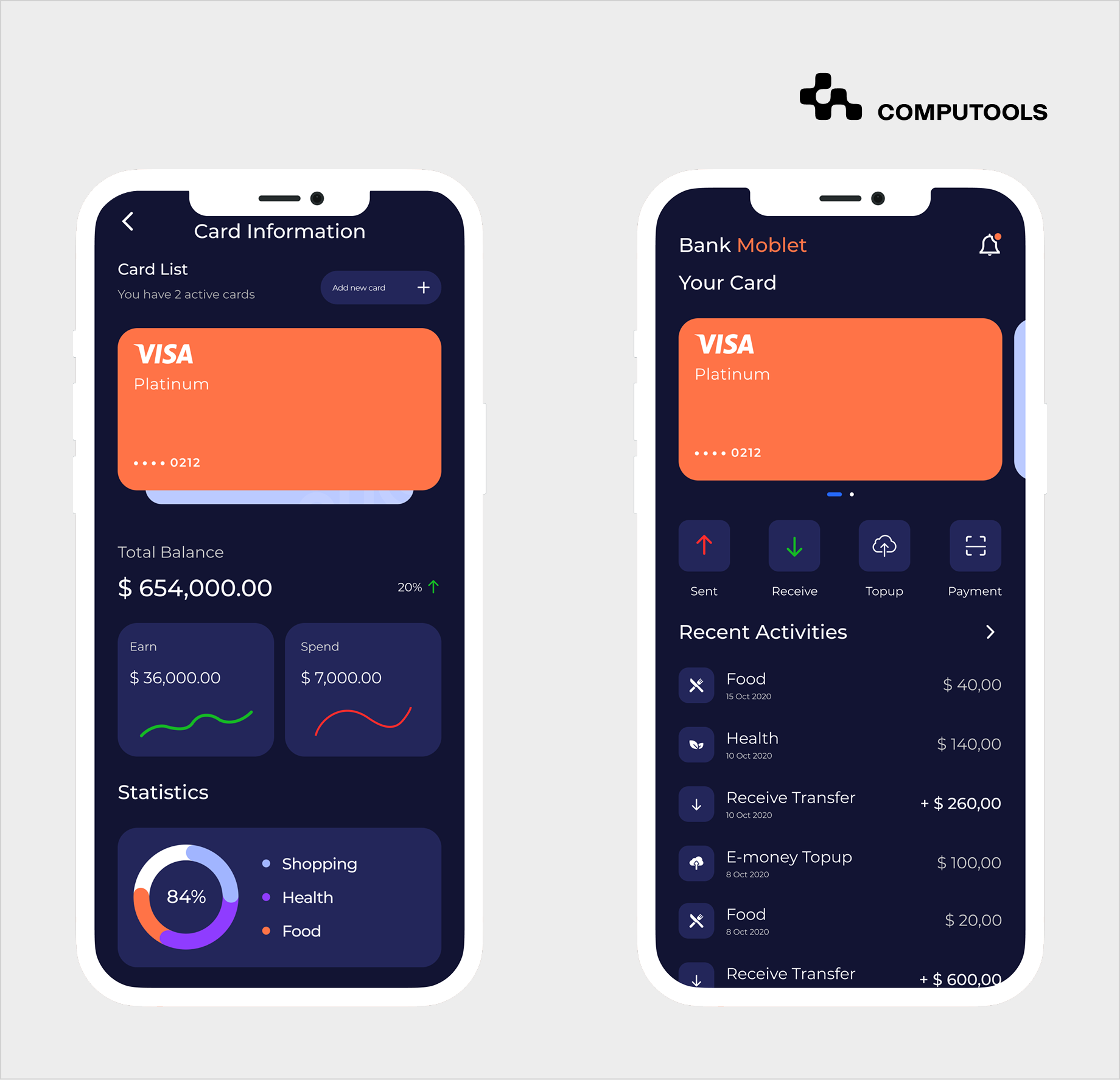
We designed the solution so that all banking and payment interactions were handled exclusively on the backend, isolating third-party APIs from the mobile layer. Integrations with SWIFT, VISA, and Mastercard were implemented with strict access controls, full audit logging, and secure token management.
At the same time, KYC and onboarding flows were unified across mobile and web, allowing Moblet to meet regulatory requirements while keeping the user journey frictionless. This balance between regulatory rigor and usability is critical in financial mobile application development, especially for fintech products aiming to scale across markets.
Step-by-step: how to build a fintech mobile app with secure banking integrations
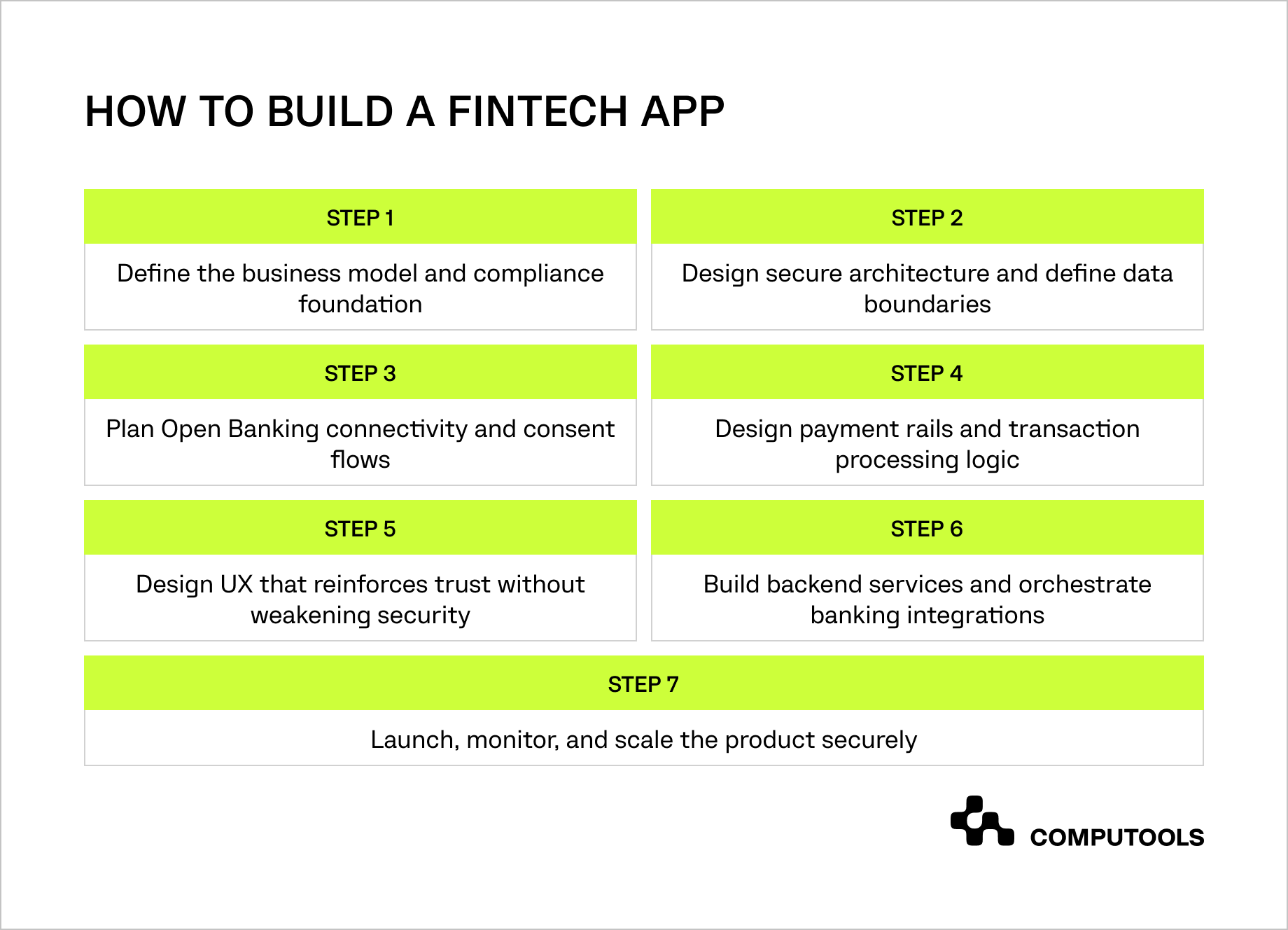
Step 1. Define the business model and compliance foundation
Every fintech product begins with decisions that define its legal, operational, and technical boundaries.
• Teams must understand the financial problem, target users, and regulatory constraints before designing the architecture. In fintech, the business model influences onboarding, data ownership, transaction logic, and possible integrations.
• Teams should identify their fintech category, such as digital banking, payments, P2P, or hybrid, and revenue model. They must also target regions and map regulations like GDPR, AML/KYC, PCI DSS, and local banking laws. These choices affect data storage, retention, audit trails, and third-party partnerships.
• Compliance should be integrated into the product plan, including responsibilities, customer consent, verification triggers, and activity reporting. Neglecting this can cause costly rework, delays, or security issues.
• A well-defined MVP focuses on core financial workflows — onboarding, identity verification, balance visibility, and transaction execution — while deferring secondary features. Clear prioritization helps align business goals with regulatory feasibility and development effort, which is especially critical in competitive fintech markets and when delivering custom fintech mobile solutions for regulated environments.
Our case Moblet was positioned as a challenger banking platform entering retail banking, treated as a regulated financial platform rather than a generic mobile app. Together with the client, we defined the product scope around core financial management use cases, account management, expense tracking, budgeting, and transaction visibility, and aligned it with compliance expectations for banking and payment integrations.
Because Moblet planned to integrate with major financial rails such as SWIFT, VISA, and Mastercard, regulatory and risk considerations shaped product decisions from day one. Onboarding flows, identity verification, and transaction visibility were designed to support auditability and transparency without compromising usability.
This early alignment eliminated architectural rework later and ensured that subsequent technical decisions reinforced, rather than conflicted with, the platform’s regulatory obligations.
Step 2. Design secure architecture and define data boundaries
Once the business model and compliance foundation are defined, the next critical step is designing a system architecture that can safely support financial operations at scale. In fintech, architecture is the primary mechanism for risk containment.
Poor architectural decisions at this stage often lead to security gaps, fragile integrations, and compliance issues that surface only after launch.
• A secure fintech architecture starts with clearly defined trust boundaries. Mobile applications should never communicate directly with banking systems or payment providers. Instead, all sensitive operations, including authentication, transaction processing, consent management, and third-party integrations, must be handled on the backend.
This separation allows teams to centralize security controls, protect credentials, enforce access policies, and maintain a complete audit trail for regulated operations.
• At this stage, teams should also define how financial and personal data flows through the system. This includes deciding which data is stored, which is processed transiently, and which must never be persisted.
Encryption strategies for data in transit and at rest, key management approaches, role-based access control, and logging policies must be agreed upon before development begins. Applying fintech app security best practices early helps avoid retrofitting controls later, when changes become expensive and risky.
• Equally important is planning for failure. Banking APIs and payment providers are not always available, and transactions may be delayed, reversed, or partially completed. A resilient architecture accounts for retries, idempotency, reconciliation jobs, and clear state transitions, ensuring financial data remains consistent even when integrations behave unpredictably.
Moblet’s secure architecture was vital for entering retail banking. We used a layered design: the mobile app handled only presentation and user interaction, while all sensitive logic was in backend services. This involves standalone integrations with SWIFT, Visa, and Mastercard, with strict access controls and monitoring.
We set clear data boundaries early. Financial data, tokens, and credentials were managed on the server with encryption and audit logs. Designing for failure scenarios such as delayed transactions or outages helped maintain data integrity and trust even under challenging conditions.
This architecture provided a stable base for future growth, integrations, and regulatory needs without major changes to the core system.
Step 3. Plan Open Banking connectivity and consent flows
Once the core architecture and data boundaries are set, the next key layer is how your fintech app connects to banks and accesses financial data. In modern fintech, bank connectivity is an ongoing process involving user consent, authentication, token management, access revocation, and regulatory traceability.
• At this stage, teams must design how users grant permission to access their financial data and how that permission is enforced across the system. This includes defining consent scopes, expiration rules, renewal logic, and user-facing controls for revoking access. Strong Customer Authentication (SCA), multi-step authorization flows, and fallback scenarios must all be considered upfront. Poorly designed consent flows are one of the most common causes of failed bank integrations and broken user journeys.
• A robust approach to open banking API integration also requires careful handling of access tokens and refresh tokens. Tokens should never be exposed to the mobile client or stored insecurely. Instead, they must be managed server-side, encrypted, rotated regularly, and revoked immediately when access is withdrawn. Teams should also anticipate edge cases such as partial data availability, delayed synchronization, rate limits, and provider outages, all of which are common in real banking environments.
• Another important aspect of this step is observability. Every interaction with a banking API should be traceable for compliance and audit purposes. This means logging who accessed what data, under which consent, and for what purpose. Without this visibility, fintech products struggle to pass regulatory reviews or to investigate user complaints about data accuracy.
In the Moblet project, banking connectivity was core, relying on multiple financial rails and external providers. We designed consent and access flows for central control and auditing. All authorization was handled on the backend, preventing mobile clients from interacting directly with banking systems or storing sensitive data.
We considered banking integration realities early, including token lifecycles, access revocation, and delays, ensuring consistent data despite external uncertainties. Embedding consent management and monitoring helped ensure regulatory compliance while maintaining a seamless user experience.
This strategy enabled Moblet to expand banking integrations securely and compliantly, essential for scaling fintech.
For teams handling cash-intensive workflows, our article, “How To Build PCI-Compliant Cash-Handling Software For Financial And Retail Operations,” explains how to design secure, audit-ready systems without slowing daily operations.
Step 4. Design payment rails and transaction processing logic
Payment processing is highly failure-prone in fintech products. Unlike data retrieval, payments are irreversible, regulated, and linked to user trust. A bug can cause double charges, stuck transactions, regulatory issues, or loss of customer confidence. Therefore, payment architecture should be deterministic, not just API calls.
• At this stage, teams need to define how funds flow through the system. This includes mapping transaction lifecycles from initiation to settlement, handling intermediate states such as pending or awaiting authorization, and defining clear outcomes for success, failure, reversal, or timeout. Payment systems must be idempotent by design, meaning the same request can be safely retried without creating duplicate transactions, a requirement when dealing with unstable networks or delayed provider responses.
• A robust payment gateway integration for fintech also requires strict separation of responsibilities. The mobile app should only initiate the intent; the backend handles validation, risk checks, routing, and final execution. Payment credentials, tokens, and provider secrets must never be exposed to the client side. Instead, the backend should orchestrate all interactions with payment networks, applying business rules, fraud checks, and compliance constraints before any funds are moved.
• Equally important is transaction observability. Every payment must be traceable across systems: who initiated it, when it was authorized, which provider processed it, and how the final status was resolved. This level of transparency is required for dispute handling, reconciliation, regulatory audits, and customer support. Without it, even a technically successful payment system becomes operationally fragile.
For Moblet, payment processing was vital to its credibility as a challenger bank. We designed flows around backend services managing SWIFT, VISA, and Mastercard interactions, ensuring transaction execution and confirmation were not dependent on the mobile client’s state.
We implemented transaction state models accounting for delays, partial confirmations, and third-party dependencies. Real-time updates and balance notifications were provided only after backend validation, reducing confusion and preventing inconsistent views. Centralized payment orchestration and strict audit logs improved operational reliability and transparency.
This approach enabled secure, real-world transactions while maintaining resilience against provider outages, network delays, and edge cases that typically disrupt less disciplined fintech systems.
Step 5. Design UX that reinforces trust without weakening security
In fintech products, UX design is inseparable from security. Users may tolerate complexity in enterprise software, but in financial apps, every extra step, unclear status, or unexpected interruption directly affects trust.
The challenge at this stage is to design user flows that are fast and intuitive while still enforcing the security controls required to handle money and sensitive data.
• This step focuses on translating complex financial logic into clear, predictable interactions. Users should always understand what is happening with their money: whether a transaction is pending or completed, why an action requires additional verification, and what to do if something goes wrong.
Security mechanisms such as biometric authentication, two-factor verification, and session timeouts must be integrated in a way that supports the user journey instead of breaking it. Poorly designed security UX often leads to unsafe workarounds, such as users disabling protections or abandoning critical flows.
• UX design in fintech must also account for edge cases. Network interruptions, delayed bank confirmations, partial transaction states, or revoked permissions should all be accurately reflected in the interface. Clear messaging and consistent visual patterns help users navigate these situations without panic or confusion. This is especially important in regulated environments, where misleading UI design can quickly become a compliance issue.
For Moblet, UX design was treated as a functional part of the system rather than a cosmetic layer. Through a custom mobile app development approach, we aligned interface decisions with backend logic, ensuring every screen accurately reflected the current state of transactions and security requirements.
The interface was intentionally minimalistic, allowing users to manage finances, track transactions, and monitor balances with minimal cognitive load.
Biometric and two-factor authentication were used for sensitive actions like accessing financial details or confirming transactions. This maintained security without complicating regular use. By aligning UX with system security, Moblet offered a simple user experience that stayed robust internally.
Step 6. Build backend services and orchestrate banking integrations
At this stage, the fintech product becomes a system rather than a set of features. Backend services enforce rules, maintain consistency, and handle external integrations, shielding users and clients from complexity. In regulated products, the backend ensures security, compliance, and reliability.
• A well-designed backend must act as an orchestration layer between the mobile application and all external providers. This includes authentication services, consent and token management, transaction processing, notification delivery, reconciliation jobs, and audit logging. Each integration should be treated as an independent component with clearly defined contracts, failure handling, and retry logic. Tight coupling to third-party APIs is one of the most common causes of fintech outages and scaling bottlenecks.
• When working with banks and payment networks, backend services must normalize inconsistent data formats, manage asynchronous responses, and handle non-deterministic behavior such as delayed settlements or partial failures. This requires message-driven processing, idempotent operations, and background workers that continuously reconcile system state with external providers. Without these mechanisms, even minor provider issues can cascade into user-visible errors and data inconsistencies.
• This is also the layer where operational transparency is established. Backend systems must produce reliable audit trails that capture who acted, what data was accessed or modified, and how external systems responded. These records are essential for compliance audits, incident investigation, customer support, and dispute resolution. Mature banking API integration services are designed with observability in mind, exposing metrics, logs, and alerts that allow teams to detect issues before users are affected.
On the Moblet platform, integrations with financial rails were managed solely through backend services; the mobile app did not interact directly with SWIFT, Visa, or Mastercard.
Backend components validated requests, applied rules, routed transactions, and processed responses asynchronously.
The system accommodated real banking behavior, including delays and provider issues, with background jobs updating transaction states and centralized logs tracking operations.
This backend approach enabled Moblet to scale, add features, and prepare for regulation without redesigning. Abstracting dependencies behind backend services provides flexibility and resilience, which are vital for fintech growth.
Step 7. Launch, monitor, and scale the product securely
Launching a fintech product tests architectural decisions under real financial pressure, exposing weaknesses not seen in staging. This phase should be a controlled operational transition, not just a one-time release.
• Before a full rollout, fintech teams should plan staged deployments with feature flags and limited user cohorts. This approach reduces risk while allowing teams to validate critical flows such as onboarding, identity verification, transaction processing, and notifications under production conditions.
Monitoring must be in place from day one, covering system health, latency, failed transactions, provider timeouts, and abnormal user behavior. Without real-time observability, even minor issues can escalate into downtime or financial loss.
• Scalability planning is equally important. As user volume grows, fintech systems face increased load on authentication services, banking integrations, and background reconciliation jobs. Teams must ensure that infrastructure scales horizontally, uses asynchronous processing where possible, and that rate limits or provider constraints do not become bottlenecks. Just as critical is incident readiness; clear runbooks, alerting thresholds, and rollback mechanisms allow teams to respond quickly without disrupting users or violating compliance obligations.
• This stage also marks the beginning of continuous improvement. Regulatory requirements evolve, banking partners update APIs, and user expectations shift. Mature fintech mobile app development processes account for this by embedding regular security reviews, compliance checks, and controlled release cycles into day-to-day operations. Fintech products that fail to institutionalize these practices often struggle to scale beyond early growth.
For Moblet, production readiness was essential. The platform was launched with monitoring and logging to track transaction behavior, authentication events, and integration performance in real time. This visibility helped detect and fix issues early. The backend supported gradual scaling and expansion without requiring changes to the mobile client.
As Moblet added features and prepared for market entry, it stayed stable, auditable, and compliant. Treating launch as the start of operations rather than the end of development, Moblet confidently expanded its technology and compliance capabilities.
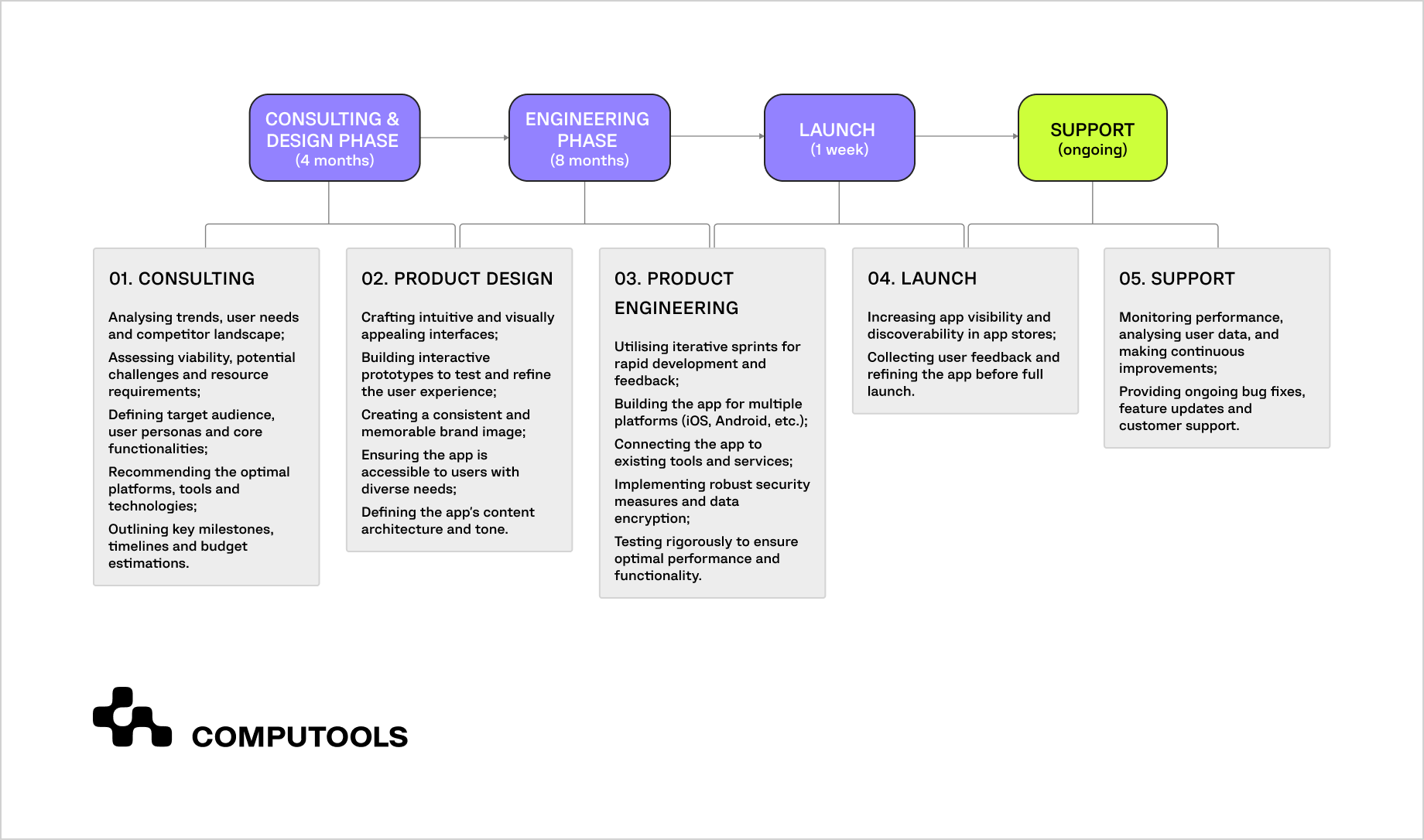
Building a fintech mobile app with secure banking integrations requires coordinated work across consulting, design, engineering, launch, and ongoing support. Below is a typical delivery timeline for a regulated fintech product, showing how strategic decisions, secure architecture, and banking integrations are distributed across phases.
Why are fintech features architectural decisions?
In fintech, every feature introduces new system responsibilities, which is why feature decisions are, in reality, architectural decisions. This is especially evident in mobile banking app development, where even small feature choices can have system-wide implications. Most fintech failures occur when teams design features first and address system responsibilities later.
• Authentication goes far beyond a login screen. Biometric access and two-factor authentication are only the visible layer. Real security lives on the backend, where sessions, tokens, access scopes, and step-up verification are enforced centrally and audited.
• Payments are stateful processes that require transaction management, idempotency, retries, and reconciliation. Decoupling execution from the UI ensures consistent payments despite network or provider failures.
• Fraud detection must be embedded into transaction flows, not added as an afterthought. Risk scoring and anomaly detection shape how and when transactions are approved, challenged, or blocked, directly influencing backend design.
• Compliance automation defines how data moves through the system. KYC, AML, and audit requirements force clear rules around data storage, access, and retention. Platforms that embed compliance into workflows scale far more easily than those that rely on manual controls.
• Personalization depends on controlled data aggregation and enrichment. Insights should be generated without exposing sensitive data or violating consent, which requires a clear separation between financial logic and analytics.
The takeaway is simple: in fintech, features are architectural commitments. Teams that treat them this way build scalable, secure systems. Teams that don’t end up rebuilding later — usually under pressure.
If your fintech roadmap also involves upgrading existing platforms, explore our guide, “How to Modernize Legacy Banking Systems Without Service Downtime,” to understand how banks can evolve without disrupting live operations.

Clarify integration paths, security controls, and development effort—request a detailed technical estimation from experienced fintech architects.
Key fintech app challenges and practical ways to address them
| Challenge | Practical solution |
| Regulatory complexity across markets. Fintech products operate under rapidly changing regulations that vary by market. Delayed attention to KYC, AML, data privacy, or licensing often leads to launch delays, rework, or blocked market entry. | Regulatory requirements should be embedded into product design and system architecture from the start. Designing onboarding, consent management, audit logging, and data retention as core workflows ensures fintech app compliance and security are enforced systematically, not through last-minute fixes. |
| Elevated security risks and sensitive financial data. Fintech apps process credentials, personal data, and real money, making them attractive targets for fraud, phishing, and account takeover attacks. Mobile environments and third-party APIs further expand the attack surface, and even minor vulnerabilities can cause lasting damage to trust. | Apply a defense-in-depth strategy that combines zero-trust principles, multifactor authentication, strong encryption, regular penetration testing, and secure SDLC practices. Security must evolve continuously as transaction volumes and threat patterns change. |
| Complex integrations with banks and payment providers. Fintech platforms rely on external banking APIs, payment gateways, and open banking services that differ in reliability, standards, and response behavior. These dependencies introduce latency, partial failures, and inconsistent data that are outside the product team’s control. | Build backend-driven orchestration layers that abstract external systems and absorb their complexity. Reliable, secure banking integrations for fintech apps require retries, reconciliation processes, centralized monitoring, and clear failure handling to prevent provider issues from surfacing in user journeys. |
| Scalability under real-time transaction load. Financial apps experience sharp traffic spikes tied to payroll cycles, instant payments, or promotional activity. Systems designed around average load often fail during peak usage, resulting in outages, customer complaints, and regulatory scrutiny. | Design cloud-native architectures with horizontal scaling, asynchronous transaction processing, and clear separation of services based on SLA criticality. Capacity planning should be based on peak behavior. |
| User trust and retention pressure. Users have little tolerance for failed transactions, unclear payment statuses, or excessive security friction. Even small usability or reliability issues can quickly erode trust and drive churn. | Focus on transparent transaction states, predictable UX flows, real-time notifications, and visible but unobtrusive security mechanisms. Trust grows when users always understand what is happening with their money. |
| Talent scarcity and delivery speed constraints. Fintech development requires expertise across engineering, security, compliance, and integrations. Scarcity of experienced specialists slows delivery and increases the risk of rushed architectural decisions. | Combine internal product ownership with experienced fintech development partners to maintain execution speed. Keep architectural control and domain knowledge in-house while using external expertise to scale delivery capacity. |
If your financial platform also touches insurance workflows or risk assessment, read how AI and automation are driving structural change across underwriting, claims, and core insurance operations.
Why businesses should work with a fintech app development company in 2026
By 2026, building a fintech product will involve more than speed. Rising regulation, high security standards, and fragmented integrations increase complexity. Managing this with a generalist team heightens technical, operational, and financial risks. This is where partnering with an experienced fintech software development company like Computools becomes a strategic decision, helping reduce risk and build for long-term scale.
1. Proven fintech and regulated-industry expertise
Computools has extensive experience developing and modernizing software for regulated sectors like banks, fintechs, insurers, and investment firms.
With over 250 engineers and 400+ projects, the team specializes in compliance, security, and large-scale system design. This experience reduces trial-and-error during delivery and helps businesses avoid architectural decisions that later become blockers during audits or scaling. Computools focuses on fintech software development services and systems that can withstand regulatory reviews, security assessments, and real production load.
This expertise is demonstrated in real-world fintech cases like Moblet, where Computools delivered a cross-platform app that provided a stable, user-friendly platform, improved clients’ financial management, and supported rapid growth.
2. Security and compliance
In fintech, retrofitting compliance or security after launch is expensive and risky. Computools embeds KYC/AML workflows, audit logging, data access controls, and security best practices directly into architecture and development processes.
This approach helps businesses meet requirements such as GDPR, PCI DSS, PSD2, and regional regulations without slowing down product delivery.
3. Strong integration and platform engineering capabilities
Modern fintech products depend on complex ecosystems: banking APIs, payment rails, identity providers, fraud systems, and analytics platforms. Computools has hands-on experience integrating with global financial networks and third-party providers, and designing backend orchestration layers that absorb external instability rather than exposing it to users.
This integration-first approach enables businesses to expand into new markets or add providers without rebuilding core systems. For example, a Caribbean bank partnered with Computools to integrate microservices for Visa card processing, attracting younger customers and increasing its market share by 12% among 18–30-year-olds through a modern digital experience.
4. Custom solutions aligned with business strategy
Off-the-shelf platforms rarely match a company’s exact operating model, risk profile, or growth plans. Computools specializes in building custom finance software that aligns technology decisions with business objectives, whether that means supporting new revenue models, scaling transaction volume, or preparing for geographic expansion.
The team combines product thinking with engineering depth to turn technical choices into long-term competitive advantages, not short-term compromises.
5. Operational maturity and long-term partnership
Beyond initial delivery, fintech products need ongoing monitoring, updates, and adaptation to regulatory and market shifts. Computools acts as a long-term partner, supporting scaling, modernization, and performance as products develop.
This maturity benefits companies aiming for sustained growth over one-off launches in volatile, regulated markets.
To sum up
In 2026, fintech success depends less on how fast you ship and more on how well your system holds up under regulatory scrutiny, security threats, and real-world scale.
Partnering with an experienced fintech development company like Computools, one that delivers end-to-end fintech app development services, helps businesses reduce delivery risk, accelerate time-to-market responsibly, and build platforms designed for long-term growth.
Computools
Software Solutions
Computools is a digital consulting and software development company that delivers innovative solutions to help businesses unlock tomorrow.








“Computools was selected through an RFP process. They were shortlisted and selected from between 5 other suppliers. Computools has worked thoroughly and timely to solve all security issues and launch as agreed. Their expertise is impressive.”