In the U.S. healthcare system, digital interactions produce protected health information (PHI), such as medication schedules and logs, linked to identifiable patients. As HealthTech data volume and sensitivity grow, architecture choices become more compliance-critical. Many products prioritize speed and usability over compliance, leading to fragmented data, excessive access, and poor auditability.
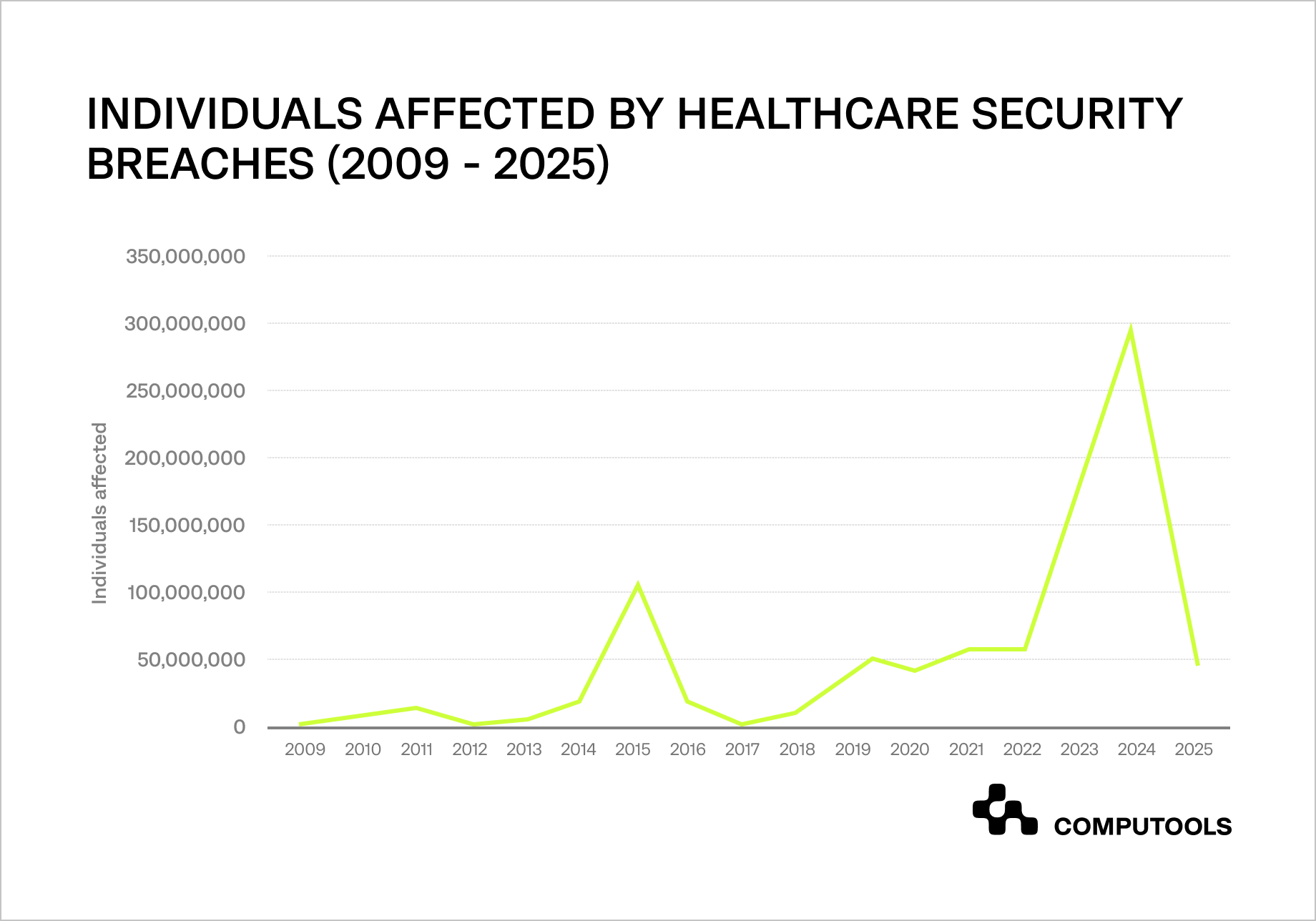
According to data compiled by the HIPAA Journal, healthcare data breaches have exposed the protected health information of over 846 million individuals since the start of breach reporting in 2009.
The trend has accelerated sharply, with over 133 million healthcare records exposed in 2023—a record then surpassed in 2024 by major incidents such as the Change Healthcare ransomware attack, bringing the total compromised records to over 276 million.
This is why designing a HIPAA compliance in healthcare software from the outset is no longer a regulatory formality, but a core business requirement for products targeting the U.S. market.
The financial impact reinforces this reality. Healthcare remains the most expensive industry for data breaches, with an average cost of $10.93 million per incident, according to IBM’s Cost of a Data Breach Report.
Based on our experience delivering HealthTech solutions for U.S.-based healthcare and pharmaceutical organizations, we have seen that a HIPAA compliant healthtech architecture is most effective when treated as a design constraint from day one rather than a post-release requirement.
To demonstrate this approach in practice, we examine TransMeds, a medication reminder application for transplant patients, where architectural decisions were driven by compliance, security, and scalability from the earliest stages of development.
How Computools worked on a HIPAA-ready medication reminder app
When a U.S.-based healthcare organization approached Computools, its primary challenge was ensuring reliable medication adherence for transplant patients while meeting strict HIPAA regulations for HealthTech platforms.
The product needed to support scheduled medication reminders, notifications, educational content, and user engagement features, all while operating in a highly regulated environment. From the outset, the system had to be secure, auditable, and scalable without introducing friction for patients.

To address these requirements, we designed and implemented TransMeds, a medication reminder application built around HIPAA-first architectural principles.
Leveraging our software architecture services, we developed a solution that clearly separates sensitive and non-sensitive data, controls access paths across all system components, and securely handles notifications and user interactions. Backend services were designed to support encrypted data storage, role-based access, and full auditability, ensuring compliance without compromising performance or usability.
At its core, TransMeds combines a robust backend architecture with an intuitive user experience. The application enables transplant patients to manage immunosuppression schedules, receive timely reminders, track medication adherence, and access educational materials. From a business perspective, the architecture supports scalability, operational transparency, and regulatory readiness, allowing the product to grow without accumulating compliance-related technical debt.
The TransMeds case demonstrates that embedding HIPAA requirements into system design from the outset enables HealthTech products to remain flexible and cost-efficient while meeting regulatory expectations. Rather than limiting development speed, compliance-driven architecture provided a stable foundation for future feature expansion, integrations, and long-term growth in the U.S. healthcare market.
With over 12 years of experience designing regulated digital products, we will outline the architectural decisions and trade-offs required to build a HIPAA-compliant cloud architecture that is secure, scalable, and ready for long-term growth in the U.S. healthcare market.
Remote patient monitoring platforms rely on continuous streams of sensitive health data, making architectural decisions around security and compliance especially important. Learn more in Remote Patient Monitoring Software Engineering: Challenges, Solutions, and Benefits.
How to design HIPAA-compliant HealthTech architecture from day one
Designing compliant healthcare products requires more than security tooling or documentation; effective healthtech software development services start with architectural decisions that account for regulatory requirements, data sensitivity, and long-term scalability from the very first sprint.
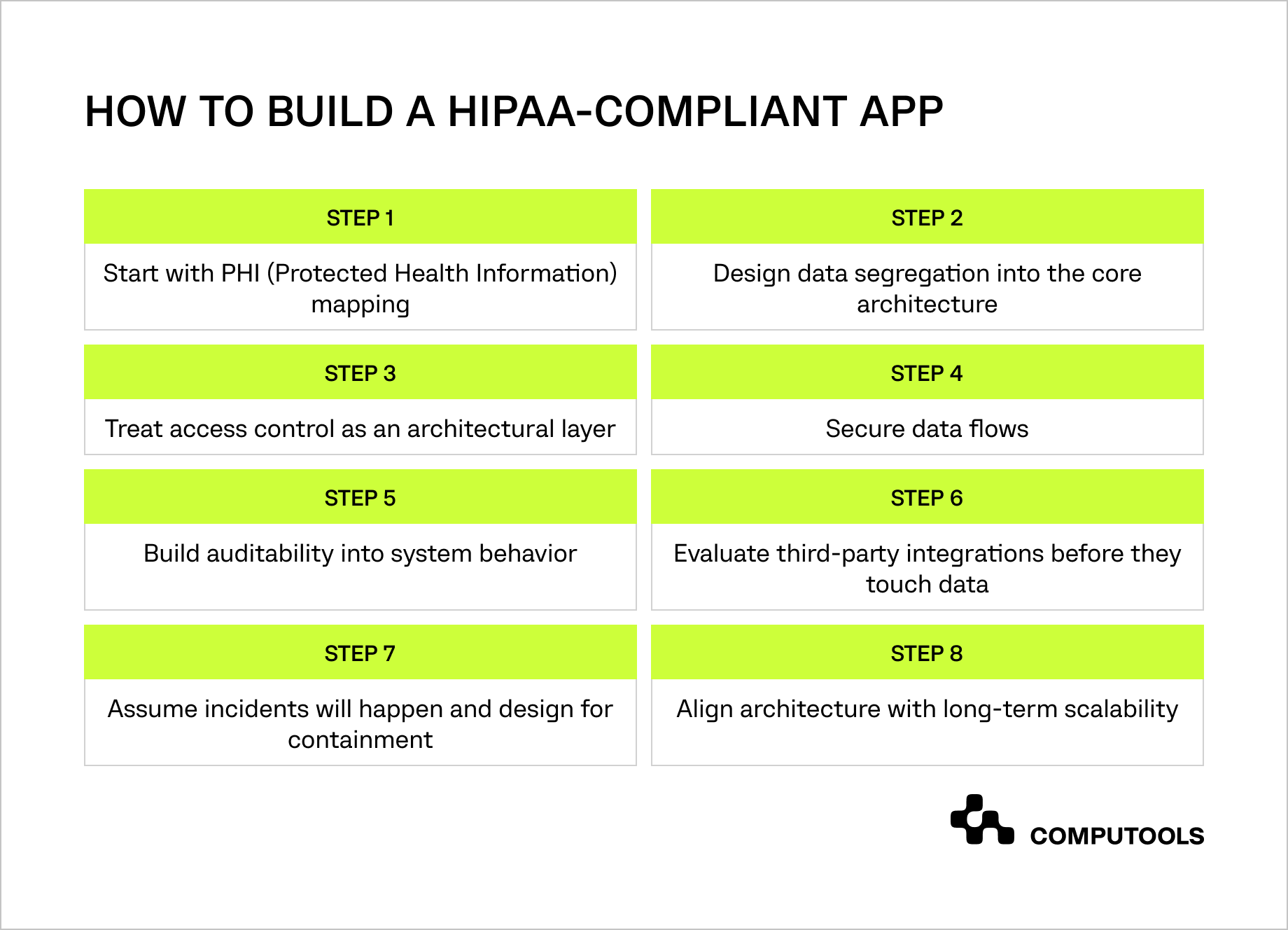
Step 1. Start with PHI (Protected Health Information) mapping
When designing a healthcare product, architectural clarity starts with understanding data exposure rather than feature delivery. Before defining services, APIs, or user flows, teams must identify which data elements qualify as protected health information, how they are generated, and how they move across the system.
Medication names, schedules, timestamps, and notifications may seem harmless in isolation, but once linked to an identifiable user, they become PHI. This mindset defines the foundation of sustainable HealthTech architecture design, preventing sensitive data from spreading across unrelated components.
In the TransMeds project, we began by mapping all data points related to medication adherence, including reminder logic and user interactions. This allowed us to define clear architectural boundaries early and avoid unintentional PHI exposure in auxiliary services.
Step 2. Design data segregation into the core architecture
One of the fastest ways to accumulate compliance risk is by allowing sensitive and non-sensitive data to share the same storage and processing paths. When data isolation is treated as an afterthought, access control, auditing, and incident response become increasingly complex. In regulated environments, proper segregation is a prerequisite for scalable HIPAA compliant software development, not an optimization.
In our TransMeds case, patient-related data was architecturally separated from non-sensitive application data at the backend level. This enabled tighter access control and ensured that engagement features and educational content never inherited unnecessary access to PHI.
Step 3. Treat access control as an architectural layer
In healthcare systems, the most common security failures are caused by internal overexposure rather than external attacks. For this reason, access management must be embedded in the system architecture rather than enforced solely through application logic. Clearly defined roles, limited privileges, and controlled service-to-service interactions are core attributes of a secure healthcare application architecture.
While working on TransMeds, we scoped access to sensitive data strictly by role and responsibility. This approach reduced internal exposure without limiting the operational flexibility required to support patients and maintain the system.
Step 4. Secure data flows
Encrypting databases alone does not protect a system where data continuously moves between services, APIs, background jobs, and notification mechanisms. Sensitive information is often most vulnerable in transit, especially in distributed systems. A resilient platform, therefore, requires a holistic healthcare data security architecture that protects data across its entire lifecycle.
In the TransMeds application, secure communication paths were designed between backend services and notification workflows. This ensured that medication reminders and user interactions were handled through encrypted and controlled channels, preserving both security and real-time responsiveness.
Step 5. Build auditability into system behavior
Healthcare organizations must be able to demonstrate who accessed sensitive data, when, and under what conditions. This level of traceability cannot be reconstructed reliably once a system is live. Auditability must be an inherent system property, forming a core element of a HIPAA compliant system design rather than a post-release addition.
For TransMeds, audit considerations were incorporated early, allowing consistent tracking of interactions with patient-related data. This created a reliable foundation for compliance reporting and incident analysis without disrupting daily operations.
Step 6. Evaluate third-party integrations before they touch data
External services are often introduced for speed and convenience, but in healthcare systems, they can quickly become compliance liabilities. Notification providers, analytics tools, and monitoring platforms must be evaluated based on how they interact with sensitive data. Following HealthTech infrastructure best practices means architecting integrations deliberately, not retroactively constraining them.
In the TransMeds project, third-party integrations were assessed and structured to avoid unnecessary exposure to PHI. This reduced dependency risk and simplified compliance management as the product evolved.
Step 7. Assume incidents will happen and design for containment
No healthcare system is immune to incidents. The difference between manageable events and regulatory crises lies in the level of architectural preparedness. Clear data boundaries, traceable access paths, and isolated components are essential characteristics of a resilient HIPAA compliant app architecture.
For TransMeds, architectural segregation and scoped access paths ensured that potential issues could be contained within defined system areas, minimizing operational disruption and regulatory impact.
Step 8. Align architecture with long-term scalability
Compliance-driven architecture should enable growth rather than restrict it. When regulatory requirements are embedded into foundational design decisions, products can evolve without revisiting core security assumptions. This is the hallmark of effective healthcare software compliance solutions in the U.S. market.
In the TransMeds case, this approach provided a stable foundation for feature expansion and user growth while maintaining regulatory readiness. Compliance was not a constraint, but a structural advantage that supported long-term scalability.
AI agents are increasingly used to automate patient interactions and clinical workflows, which introduces new requirements for data security, governance, and compliance. Learn more in AI Agents in Healthcare Industry: Smarter Automation for Better Patient Experience.

See how designing compliance-first HealthTech systems creates a foundation for secure data exchange, interoperability, and sustainable growth.
What mistakes should be avoided to maintain HIPAA Compliance?
Even teams with strong technical backgrounds can run into compliance issues when decisions that seem safe in development create risk as the product scales.
1. Relying on default cloud configurations. Cloud environments are optimized for fast deployment, not regulated workloads. Without deliberate security hardening, sensitive data may be more exposed than expected.
2. Using third-party tools without strict data boundaries. SDKs, analytics platforms, and notification services can unintentionally handle PHI if data flows are not explicitly controlled at the architectural level.
3. Working with real patient data outside production. Development and testing environments should never process live or insufficiently anonymized health data, as they rarely meet production-level security standards.
4. Weak session and access lifecycle management. Long-lived sessions and improperly revoked access tokens increase the risk of unauthorized access, even in systems with otherwise strong security controls.
5. Choosing teams without healthcare compliance experience. HIPAA compliance requires both technical and regulatory expertise. A lack of domain experience often leads to architectural gaps that are costly to fix later.
Benefits of HIPAA compliance for healthcare providers
Modern hospitals handle millions of digital transactions annually, including records, prescriptions, lab results, insurance claims, and patient communication. Security failures usually result from architectural flaws, permissive access, data mishandling, or poor integration governance, risking large-scale data breaches.
This is why HIPAA compliance cannot be treated as a policy layer added on top of existing systems. It must be embedded directly into the Healthcare IT security architecture. Healthcare remains the most expensive industry for data breaches, with the average incident costing $10.93 million. Architectures that enforce encryption by default, minimize access paths, and provide end-to-end traceability significantly reduce both breach likelihood and financial impact.
• Beyond cost, compliance directly affects trust. Research consistently shows that a substantial portion of patients are willing to change providers after a data breach. In practice, reputational damage often occurs long before fines or legal actions follow. Organizations that demonstrate strong privacy safeguards, rapid incident detection, and transparent response processes signal that patient confidentiality is treated with the same seriousness as clinical outcomes.
• HIPAA compliance also delivers operational benefits. Standardized data handling enables automation across claims processing, eligibility checks, and authorizations—areas that still generate heavy administrative overhead. These gains are only achievable when systems are designed to exchange data securely and consistently across organizational boundaries.
• Interoperability is another critical advantage. Secure data sharing across EMRs, laboratories, pharmacies, and patient-facing applications enables hospitals to coordinate care more quickly while maintaining strict control over electronic protected health information. In contrast, fragmented or legacy integrations often force a trade-off between accessibility and security.
Benefits of HIPAA compliance for patients
For patients, HIPAA is not an abstract regulation; it is protection against losing control over deeply personal information. Medical data privacy is widely perceived as a fundamental right, and tolerance for misuse or exposure is extremely low. When records are logged, encrypted, and traceable, patients gain confidence that their medical histories cannot be accessed or altered without accountability.
• HIPAA also gives patients visibility and agency. Compliant systems allow individuals to understand who accessed their data, request corrections, and limit future disclosures. When these capabilities are delivered through clear digital workflows rather than manual processes, compliance becomes a tangible experience rather than a legal promise.
• There is also a direct connection between HIPAA compliance and fraud prevention. Healthcare records are highly valuable on illicit markets, and breaches frequently lead to identity theft, false insurance claims, and unauthorized medical services. Systems designed with strong authentication and anomaly detection significantly reduce the risk of such abuse.
• Finally, compliant interoperability improves care itself. When secure data exchange allows clinicians to access complete, up-to-date records regardless of where care was previously delivered, diagnostic delays shrink, and coordination improves.
How HIPAA compliance supports long-term platform growth
As healthcare organizations evolve, HIPAA compliance increasingly intersects with broader transformation initiatives. Legacy platforms often fail to meet modern security and scalability requirements, pushing teams toward software modernization that rethinks data flows, access models, and integrations without disrupting care delivery.
This is particularly evident in pharmaceutical software development, where products must balance strict regulatory oversight with high availability, real-time data exchange, and patient engagement. In these environments, compliance-driven architecture becomes a growth enabler rather than a constraint.
Why choose Computools for HIPAA-compliant HealthTech architecture
Designing HIPAA-compliant HealthTech platforms requires architectural experience grounded in real-world regulatory constraints, not theoretical best practices. With over 12 years of experience delivering solutions for regulated industries, Computools helps healthcare products scale securely by embedding compliance into system design from the very beginning.
Our work on projects like TransMeds demonstrates how compliance-first architecture supports real use cases such as medication adherence, secure notifications, and patient engagement without compromising usability or time-to-market. We combine deep domain expertise with digital transformation services to modernize healthcare platforms, redesign data flows, and build systems that remain audit-ready as they grow.
From backend architecture to mobile app development, we design HealthTech products that balance security, performance, and scalability. Choosing Computools means working with a partner who treats HIPAA compliance as a strategic foundation for long-term growth, not a post-launch obstacle.
Selecting the right development partner is critical to building compliant, scalable healthcare solutions. We have compiled a curated list of the leading companies shaping the industry. Read more in Top 25 Healthtech Software Development Companies in 2026.
Conclusion
Designing HealthTech systems for the U.S. market requires more than functional delivery. HIPAA compliance directly influences architecture, scalability, and long-term business viability.
When compliance is embedded into system design from day one, products avoid costly rework, reduce regulatory risk, and scale with confidence. A well-designed Secure PHI data architecture turns compliance from an obligation into a structural advantage that supports growth rather than slows it.
Computools
Software Solutions
Computools is an IT consulting and software development company that delivers innovative solutions to help businesses unlock tomorrow.








“Computools was selected through an RFP process. They were shortlisted and selected from between 5 other suppliers. Computools has worked thoroughly and timely to solve all security issues and launch as agreed. Their expertise is impressive.”