Enterprise cybersecurity financial services have become a baseline operational requirement for financial institutions. According to Statista, the global information security market exceeded $200 billion, with enterprise security software remaining the largest segment and projected to grow from $78.8 billion in 2024 to $132.4 billion by 2028, reflecting sustained investment in centralized, scalable security controls.
Recent data from IBM shows that the global average cost of a data breach declined to $4.44 million in 2025, driven by faster detection and containment enabled by AI-powered defenses.
However, regional and structural risks remain significant. In the United States, average breach costs rose to $10.22 million, largely due to higher regulatory penalties and investigation costs.
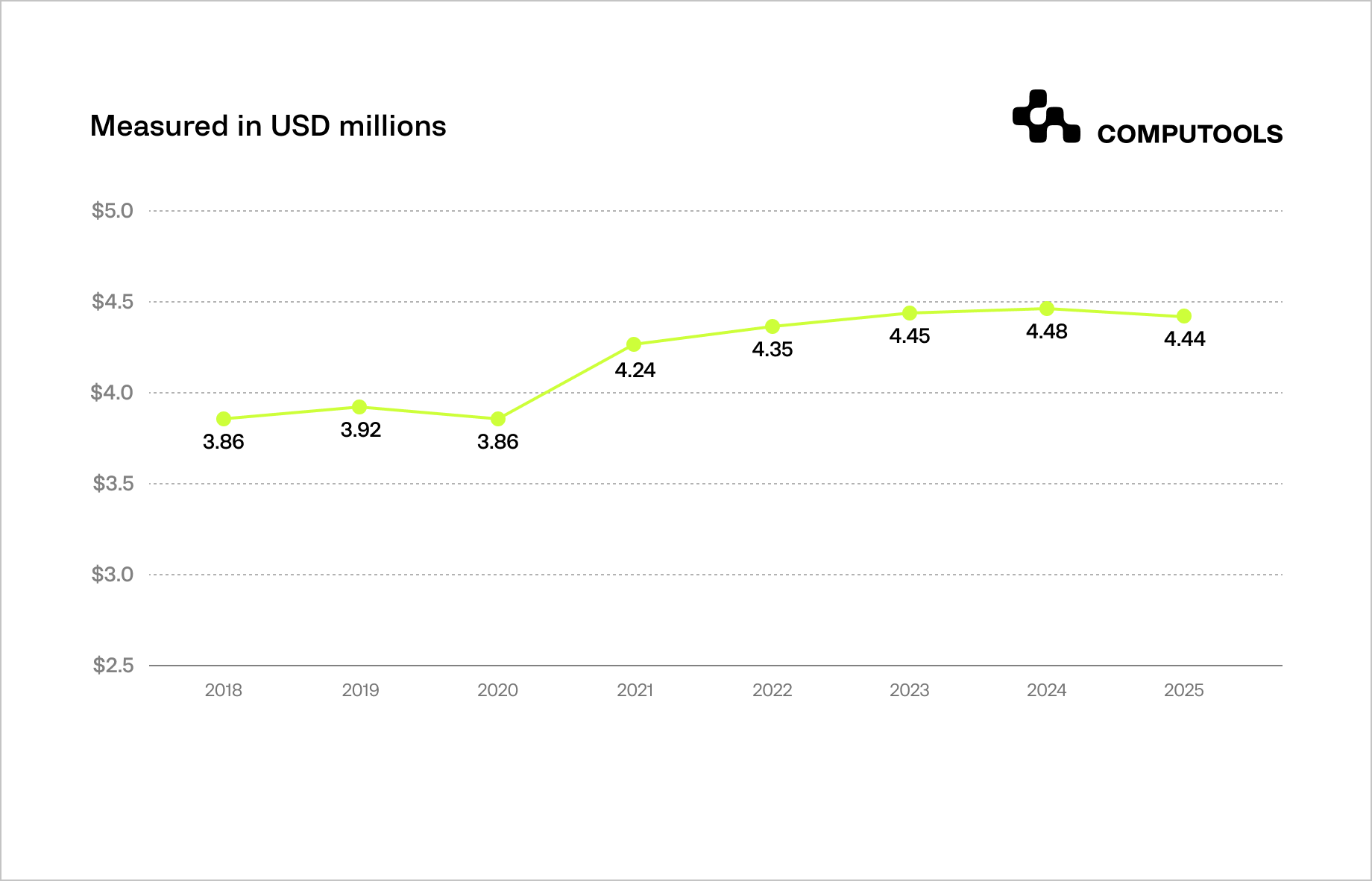
In Q2 2024, organizations experienced an average of 1,636 cyberattacks per week, a 30% year-over-year increase, highlighting both the scale and persistence of modern threat activity. AI is reshaping both defense and attack. 16% of breaches involved AI-enabled attackers, primarily through phishing and impersonation.
At the same time, 97% of AI-related breaches occurred in organizations without proper AI access controls, and 63% lacked formal AI governance policies. Incidents linked to shadow AI added an average of $670,000 to breach costs.
According to Gartner, cloud intrusions increased by 75% year over year, while decentralized technology usage continues to expand the attack surface. By 2027, 75% of employees are expected to acquire or modify technology outside centralized IT control.

These conditions set the baseline for an effective financial services cybersecurity strategy, requiring enterprise-wide visibility, continuous threat detection and prevention, and governance that extends beyond individual tools.
Strong cybersecurity is also a key driver of trust in digital finance. For a broader view on how security, UX, and reliability shape long-term relationships, see our Ultimate Guide to Building Customer Loyalty in the Digital Banking Industry.
How we implemented enterprise cybersecurity for a multi-country financial services group
A practical example of how enterprise cybersecurity is implemented in financial services comes from Generation Group, an international banking holding operating across the USA, Canada, the UK, Germany, and Australia.
The company works with large volumes of sensitive financial and customer data and supports banking operations across multiple jurisdictions. As attack techniques became more sophisticated, the organization faced increased exposure across endpoints, internal networks, and customer-facing digital systems.
To address these risks, the client expanded its security capabilities and transitioned from fragmented controls to an integrated enterprise model. Our team joined the client to deliver centralized cybersecurity services, focused on protecting digital assets, reducing attack success rates, and maintaining continuous security visibility across regions.
The implemented solution combined continuous network monitoring through a Threat Detection System (IDS), real-time attack blocking via an Intrusion Prevention System (IPS), enterprise endpoint protection, and a vulnerability management platform.
An Information Security Management System (ISMS) was implemented in parallel to formalize security policies, incident response workflows, and compliance with ISO/IEC 27001 requirements. Detection logic, prevention mechanisms, and governance processes were designed to operate as a single system rather than isolated tools.
Impact
• 71% reduction in the likelihood of successful cyberattacks due to improved threat detection accuracy
• 50% reduction in incident response time through optimized penetration testing and remediation workflows
• Improved protection of sensitive banking data across endpoints and internal systems
• Increased customer confidence in online banking services
This case demonstrates how enterprise-level financial data security can be achieved through an integrated enterprise cybersecurity approach that aligns detection, prevention, and governance across the organization.
How to implement enterprise cybersecurity for financial services companies
The following steps reflect practical patterns observed across enterprise cybersecurity financial services initiatives, shaped by real-world implementations and operational constraints.
Step 1. Map and control the external attack surface
The starting point for cybersecurity implementation for enterprises is gaining clear visibility into the external attack surface. For financial services companies, this surface includes public-facing domains, APIs, cloud workloads, third-party services, and unmanaged or forgotten assets that have accumulated over time.
Large financial organizations face a constantly changing attack surface due to new cloud resources, vendor onboarding, and exposed APIs across regions. Asset inventories quickly become outdated, creating blind spots attackers exploit.
External Attack Surface Management (EASM) continuously discovers and monitors internet-facing assets, helping security teams identify exposed systems, misconfigurations, leaked credentials, and fraudulent domains before abuse.
For financial institutions, EASM typically focuses on:
• exposed banking portals and APIs,
• leaked credentials and sensitive data indicators,
• unused or misconfigured cloud assets,
• brand impersonation and phishing infrastructure.
This visibility enables security teams to prioritize remediation based on real exposure rather than assumptions, forming the foundation of effective Enterprise-level financial data security. Instead of reacting to incidents after compromise, organizations can remove entry points early and reduce downstream risk.
In the Generation Group case, external asset discovery was a prerequisite for strengthening security across multiple regions. Continuous monitoring of exposed assets allowed the team to eliminate high-risk entry points before integrating detection, prevention, and governance layers later in the program.
Step 2. Establish enterprise-grade identity and access control
At enterprise scale, identity becomes the primary security perimeter. Financial services organizations operate across internal teams, external vendors, cloud platforms, and customer-facing systems, making uncontrolled access one of the most common breach vectors.
The goal of this step is to implement consistent, identity-centric controls across all environments. This includes mandatory multi-factor authentication for employees, administrators, and third-party users, strict role-based access control, and centralized provisioning and de-provisioning workflows. Access must be tied to verified identities, device context, and business roles rather than network location.
In large financial enterprises, access complexity increases with mergers, geographic expansion, and outsourcing. Without centralized control, dormant accounts, excessive privileges, and shared credentials accumulate over time. These conditions directly increase exposure to credential abuse, lateral movement, and insider threats.
Enterprise identity and access management supports financial services IT security solutions by limiting blast radius. Even when credentials are compromised, least-privilege enforcement prevents attackers from accessing critical systems or sensitive financial data.
In the Generation Group implementation, tightening access controls across endpoints and internal systems reduced credential-based risk and established a stable foundation for continuous monitoring and threat prevention in subsequent steps.
Step 3. Implement continuous threat detection and prevention
Once access is controlled, enterprise cybersecurity must focus on continuous visibility and response. In financial services environments, threats often bypass perimeter defenses through compromised credentials, misconfigurations, or third-party access. This makes ongoing detection and prevention critical at an enterprise scale.
This step involves deploying coordinated detection and prevention mechanisms across the network, endpoints, and critical systems. Intrusion Detection Systems (IDS) provide real-time visibility into abnormal traffic and suspicious behavior, while Intrusion Prevention Systems (IPS) automatically block confirmed threats before they escalate into incidents.
For large financial organizations, the challenge is making sure they function as a single system. Detection signals must feed directly into prevention workflows, incident response processes, and security operations teams. Fragmented monitoring leads to delayed response and incomplete containment.
Effective detection and prevention are core components of financial industry cybersecurity solutions, enabling early attack identification, faster containment, and reduced operational impact.
In the Generation Group case, combining IDS and IPS into a single operational system decreased the chances of successful cyberattacks by 71%, showing the value of coordinated, company-wide threat detection instead of separate controls.
Many cybersecurity threats to financial institutions originate from outdated platforms that are difficult to patch or monitor. For a practical way to upgrade core systems without stopping live operations, see How to Modernize Legacy Banking Systems Without Service Downtime.
Step 4. Implement vulnerability management and penetration testing
In enterprise financial environments, vulnerabilities accumulate continuously due to system complexity, frequent updates, and third-party integrations. Treating vulnerability management as a periodic audit creates long exposure windows that attackers actively exploit.
This step focuses on embedding vulnerability management into day-to-day security operations. It includes continuous scanning, risk-based prioritization, and structured remediation workflows aligned with asset criticality. Penetration testing complements scanning by validating real-world exploitability and testing incident response readiness.
For financial services companies, vulnerability data must directly inform security operations and risk decisions. Findings should be traceable to system owners, remediation timelines, and measurable outcomes rather than static reports. This approach strengthens enterprise risk management in financial services by reducing the time between vulnerability discovery and mitigation.
In the Generation Group implementation, optimized penetration testing and remediation workflows reduced incident response time by 50%, limiting the impact of emerging threats.
Step 5. Secure endpoints across distributed financial operations
Endpoints remain a primary attack vector in financial services due to remote work, mobile access, and third-party usage. Enterprise cybersecurity must provide consistent endpoint protection across employee workstations, administrative devices, and mobile environments.
This step involves deploying centralized endpoint protection, behavioral monitoring, and device hardening, with visibility integrated into detection and response workflows. Endpoint security should not operate in isolation but as part of a coordinated enterprise security model.
In large organizations, unmanaged or inconsistently protected endpoints create gaps that undermine broader security controls. Standardizing endpoint security reduces exposure to malware, credential theft, and lateral movement.
Effective endpoint protection directly supports data protection for financial institutions by reducing the risk of data leakage and unauthorized system access.
For Generation Group, strengthening endpoint security improved the protection of customer data and increased confidence in online banking services.
Step 6. Embed governance through an enterprise cybersecurity framework
As technical controls mature, financial organizations need governance to ensure consistency, accountability, and regulatory alignment. Without a formal framework, security decisions remain fragmented and difficult to audit at an enterprise scale.
This step focuses on implementing an Information Security Management System (ISMS) to define policies, roles, risk assessment processes, and incident response procedures across the organization. An ISMS aligned with ISO/IEC 27001 enables financial institutions to manage security as a continuous, measurable process rather than a set of isolated initiatives.
For large financial services companies, governance provides a common structure for evaluating risk, prioritizing investments, and demonstrating compliance across regions and regulators. It also ensures that detection, prevention, and response activities are coordinated and repeatable. Embedding governance through a formal cybersecurity framework for financial services allows security teams to translate technical controls into auditable outcomes and operational discipline.
In the Generation Group case, implementing ISMS established clear ownership, standardized security processes, and ensured ongoing compliance readiness while supporting enterprise-wide security operations.
Step 7. Manage third-party and supply chain risk
Financial services organizations rely heavily on third-party vendors, cloud providers, payment processors, and technology partners. Each external dependency introduces additional risk that extends beyond the organization’s direct control.
This step focuses on establishing structured third-party risk management across the enterprise. It includes risk-based vendor assessments, clearly defined security requirements in contracts, continuous monitoring of vendor posture, and formal offboarding procedures to revoke access when relationships end.
At enterprise scale, third-party risk must be treated as part of the overall security program rather than a procurement or compliance task. Security teams need visibility into what data vendors access, how they protect it, and how incidents are reported and managed.
Effective supplier oversight strengthens enterprise cyber risk management by reducing exposure to indirect breaches, data leaks, and supply chain attacks.
In the Generation Group implementation, third-party controls were integrated into the broader security governance model, helping ensure consistent protection across external services supporting banking operations.
Step 8. Apply Zero Trust across internal and corporate systems
As financial organizations scale across cloud platforms, remote teams, and distributed IT infrastructures, perimeter-based security models become less effective. Zero Trust Architecture addresses this by assuming that no user, device, or system should be trusted by default.
This step focuses on enforcing continuous verification for all access requests to internal tools, corporate systems, and sensitive data. Access decisions are based on identity, device posture, role, and context rather than network location. Core components include identity-centric access policies, micro-segmentation, mandatory multi-factor authentication, and continuous activity monitoring.
For enterprise financial services, Zero Trust reduces the impact of credential compromise and limits lateral movement inside the organization. Even when an attacker gains initial access, strict segmentation and verification prevent escalation to critical banking systems.
Adopting Zero Trust enhances financial services IT security by integrating access control, monitoring, and response into a unified, adaptable security framework ideal for modern enterprise environments.
Step 9. Build resilience through backup and recovery controls
Even with mature preventive and detection controls in place, financial organizations must plan for disruption. Ransomware, destructive attacks, and system failures make recovery capabilities a core component of cybersecurity for financial services companies, not an operational afterthought.
This step focuses on implementing enterprise-grade backup and recovery controls that support business continuity. Backups must be encrypted, isolated from production environments, and stored off-site to prevent attackers from tampering with recovery data. Financial institutions should avoid shared credentials or network paths between primary systems and backups.
At enterprise scale, backup strategies must align with clearly defined Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO). These metrics ensure that critical banking systems and customer services can be restored within acceptable operational and regulatory thresholds. Regular testing is essential to validate recovery procedures and avoid false confidence.
In our case, backup and recovery were treated as part of the overall security architecture rather than a standalone IT function. This approach reduced operational risk and ensured service continuity across distributed banking operations, even under adverse conditions.
Step 10. Strengthen security awareness and operational readiness
Technical controls alone cannot eliminate risk in large financial organizations. Human behavior remains a major factor in security incidents, particularly in environments with complex processes, time-sensitive operations, and access to high-value financial systems.
This step focuses on building sustainable security awareness and operational readiness across the enterprise. Financial institutions should implement mandatory, role-based training that reflects real attack scenarios, including phishing, social engineering, and credential abuse. Training must be continuous and adapted to different user groups, from frontline staff to administrators and executives.
Beyond training, organizations should establish clear reporting paths for suspected incidents, conduct regular simulations, and ensure that response procedures are understood and rehearsed. These measures help reduce reaction time and limit the impact of human-driven incidents.
Embedding security awareness into daily operations supports secure digital transformation in financial services by ensuring that people, processes, and technology evolve together rather than creating new exposure as systems modernize.
In the Generation Group case, structured awareness initiatives complemented technical controls, reducing preventable incidents and reinforcing enterprise-wide security discipline.
Key Takeaways
• Enterprise cybersecurity in financial services must be managed as an organization-wide program, not a collection of disconnected tools.
• Full visibility into external exposure is essential to reducing risk before attacks reach core financial systems.
• Identity-centric controls, continuous detection, and prevention significantly limit the impact of credential-based attacks.
• Governance, third-party oversight, and resilience planning are as critical as technical defenses for regulatory and operational stability.
• A coherent сybersecurity architecture for finance enterprises enables secure growth, compliance readiness, and long-term digital transformation.

Translate regulatory and threat requirements into a practical security architecture. Request a technical assessment and implementation estimate.
Enterprise cybersecurity financial services: consequences and threat landscape
Cyber incidents in finance have multi-layered consequences for technical recovery. Beyond direct financial losses, institutions face investigations, system restoration, notifications, and security upgrades, which strain budgets and delay strategies.
IBM’s industry analysis shows that the financial sector consistently ranks among the industries with the highest data-breach costs, reflecting the sensitivity of financial data and the complexity of restoring regulated systems.
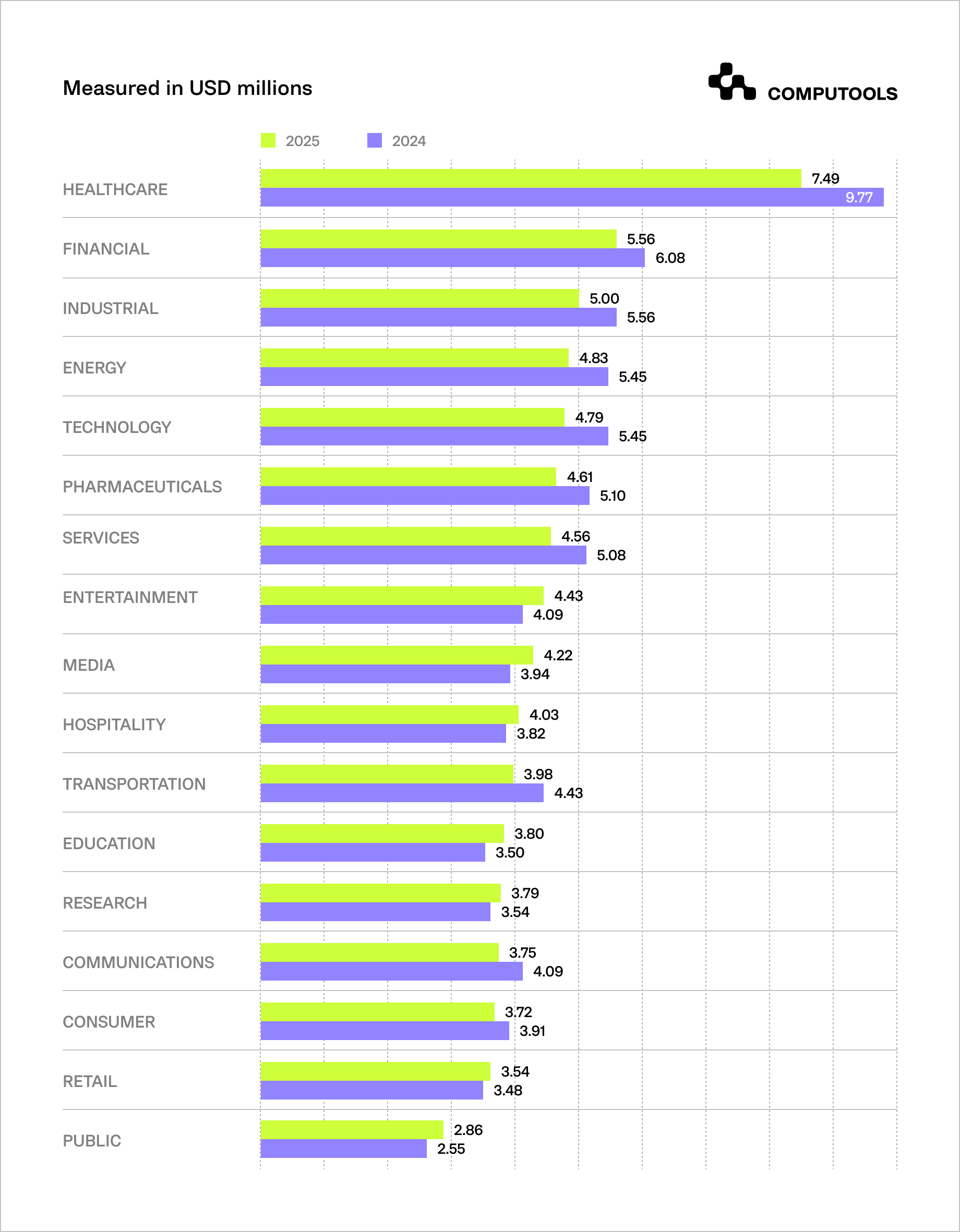
1. A critical risk specific to finance is systemic interdependence. Research by the Federal Reserve Bank of New York highlights the potential for cascading effects across the financial ecosystem. Its modeling indicates that a cyber incident affecting one of the largest U.S. banks could disrupt nearly 38% of the national financial network, turning a localized breach into a broader market event.
2. Operational disruption compounds these risks. Cyber incidents can disrupt online banking, payment processing, and trading platforms, resulting in service downtime, revenue loss, and customer dissatisfaction. In parallel, reputational damage often outlasts the technical incident itself. Trust is foundational in financial services, and once eroded, it can take years to rebuild.
3. Financial institutions also face heightened regulatory exposure following cyber incidents. Penalties, mandatory remediation, and increased supervisory scrutiny are common, particularly for organizations operating across multiple jurisdictions with differing compliance requirements.
4. The threat landscape itself continues to diversify. In addition to financially motivated cybercrime, financial institutions are targeted by state-sponsored actors seeking economic disruption and by hacktivist groups seeking visibility and impact rather than profit. High-profile campaigns against global payment networks such as Visa and Mastercard illustrate how financial services firms become symbolic and strategic targets.
5. Cloud adoption and hybrid infrastructures further complicate defense. Distributed environments introduce visibility gaps, inconsistent policy enforcement, and challenges in coordinating detection and response across platforms. In this context, enterprise security solutions for finance are essential to maintain consistent control, unified monitoring, and coordinated incident response across complex financial ecosystems.
For financial institutions, cybersecurity is vital for survival. It prevents market collapses, ensures compliance, and maintains customer trust, which, once lost, can take years to rebuild.
How to choose a cybersecurity partner for financial services
• Regulatory-first mindset. The partner must design security controls with audits, reporting, and regulatory oversight in mind from day one, not retrofit compliance later. Proven experience with cybersecurity compliance for financial institutions is essential.
• Enterprise-scale architecture experience. Financial environments span legacy systems, cloud platforms, third-party integrations, and real-time transaction flows. The partner should demonstrate the ability to secure complex, distributed architectures without fragmenting visibility or response.
• Deep system integration capability. Cybersecurity must be embedded into core banking and operational systems. Experience in fintech software development services enables security to be integrated without degrading performance or slowing product delivery.
• Business-impact orientation. Security decisions should be tied to measurable outcomes such as reduced incident likelihood, faster response times, and improved audit readiness.
• Long-term delivery and maturity support. Financial cybersecurity programs evolve continuously. The right partner supports ongoing improvement, knowledge transfer, and operational maturity rather than one-off implementations.
For a broader view of vendors operating at the intersection of fintech, security, and enterprise delivery, see our Top 25 Fintech Software Development Companies in 2025 overview.
Why Computools can support enterprise financial cybersecurity programs
Computools brings over 12 years of experience, a team of 250+ professionals, and 400+ delivered projects worldwide, including 20+ projects in the financial sector. We work with banks, fintechs, insurers, and investment firms, delivering secure, scalable solutions tailored to regulatory and operational realities.
Our expertise spans custom finance software development across digital banking, transaction monitoring, AI-powered risk assessment, loan origination, payment processing, investment management, and compliance platforms. This allows us to embed cybersecurity directly into financial systems, rather than treating it as an external layer.
We combine security engineering, enterprise architecture, and governance design to help financial organizations:
• strengthen security without disrupting operations,
• align technology decisions with regulatory requirements,
• reduce operational risk while enabling digital growth.
If you are planning or reassessing an enterprise cybersecurity initiative for financial services, we are ready to discuss how our experience can support your goals. Contact us info@computools.com.
Computools
Software Solutions
Computools is a digital consulting and software development company that delivers innovative solutions to help businesses unlock tomorrow.








“Computools was selected through an RFP process. They were shortlisted and selected from between 5 other suppliers. Computools has worked thoroughly and timely to solve all security issues and launch as agreed. Their expertise is impressive.”