Global financial institutions are under enormous pressure to modernize legacy banking systems while maintaining uninterrupted service availability. According to International Data Corporation, global digital transformation spending will reach nearly $4 trillion by 2027, growing at a 16.2% CAGR and accounting for the majority of information and communication technology investments.
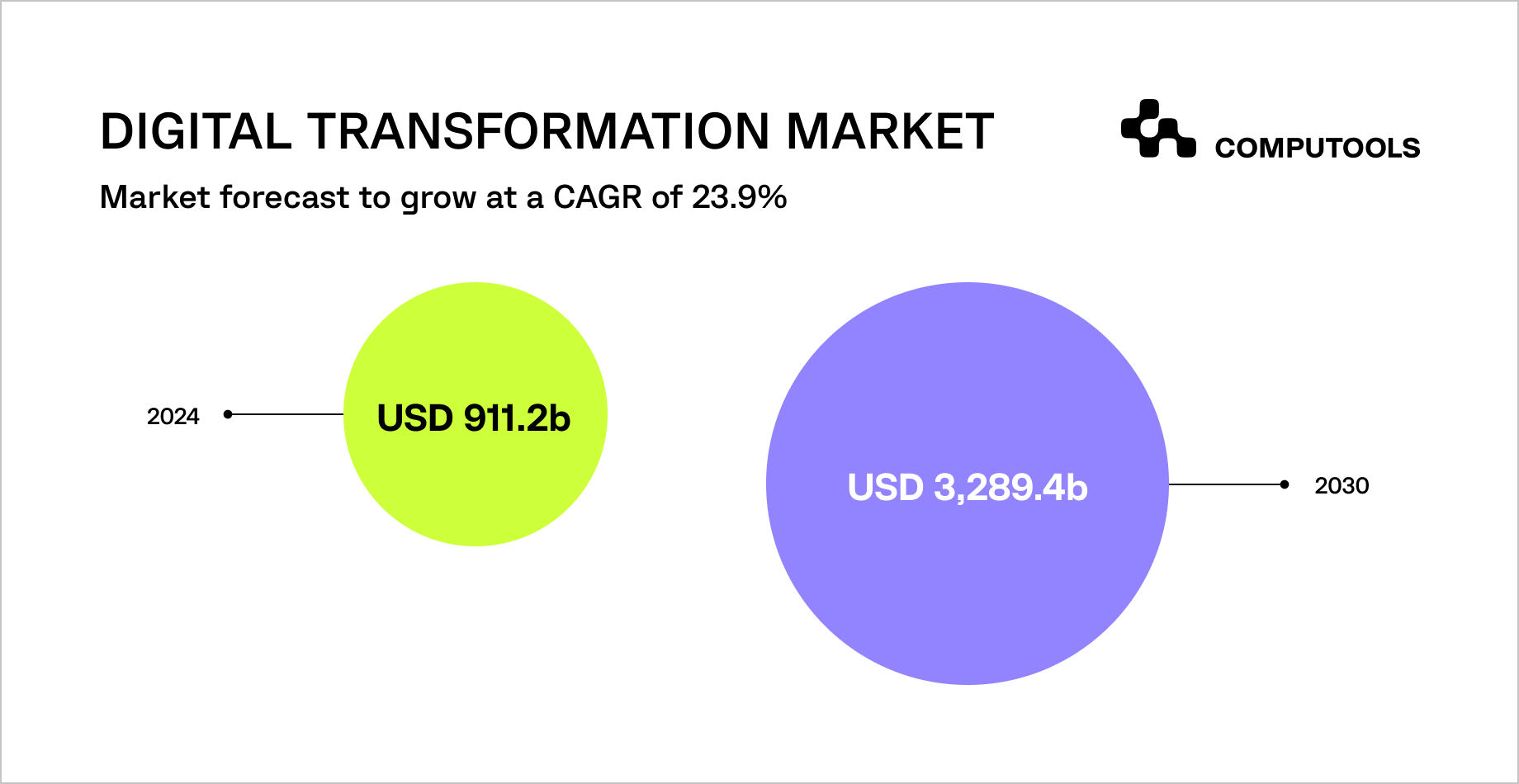
This trajectory aligns with broader market forecasts indicating continued acceleration beyond 2027, with the digital transformation market projected to reach $3.29 trillion by 2030, driven by enterprise-wide modernization initiatives.
Despite this momentum, modernization in banking remains high-risk. More than 60% of core banking modernization initiatives are delayed or fail to meet expectations, while legacy platforms consume up to 78% of IT budgets to keep existing systems operational.
The business impact is direct: 47% of customers switch banks due to weak digital services, and regulators issued $189 million in fines in the first half of 2023, many linked to system changes and compliance breakdowns during transitions.
This is why banking IT modernization strategies can no longer rely on disruptive, “big-bang” replacements. Banks must evolve tightly coupled legacy cores without downtime while balancing regulatory exposure, customer experience, and operational continuity. Institutions that achieve this report up to 45% higher operational efficiency and 30–40% cost reductions within the first year, proving that modernization without service disruption is not only possible, but commercially decisive.
How we modernized banking services for the Caribbean Bank
A leading regional financial institution, Caribbean Bank needed to expand digital banking capabilities while operating across 17 countries and serving 500K+ customers, without risking service disruption or regulatory exposure. The bank lacked in-house capacity to execute large-scale transformation and faced recurring delays in integrating with Visa within standard release cycles.
To modernize legacy banking systems without destabilizing core operations, Computools applied its fintech software development services to design a microservices-based modernization layer around the existing core. Instead of replacing critical systems, this approach enabled secure Visa integration while keeping day-to-day banking services fully operational.
The solution allowed transaction authorization, payment processing, and fund disbursement to be introduced incrementally, preserving platform stability and ensuring PCI DSS compliance throughout the rollout.
The modernization was delivered through:
• decoupled microservices architecture for card processing,
• parallel operation of legacy and new components,
• containerized deployment using Docker and Kubernetes,
• infrastructure automation with Terraform to reduce operational risk.
Business impact
• Seamless rollout of card transaction capabilities with no service downtime.
• 12% increase in market share among customers aged 18–30.
• Improved scalability and release velocity without core system replacement.
• Higher customer engagement driven by redesigned web and mobile interfaces.
This case illustrates a repeatable approach to modernizing legacy banking systems without downtime. In the next section, we break down the process step by step, showing how banks can apply the same principles to modernize legacy systems without disrupting live services.
How to modernize legacy banking systems without service downtime: step-by-step
Step 1. Start with deep discovery before touching production systems
Downtime-free modernization starts with facts, not assumptions. Before any code changes, banks must build a precise understanding of how their systems actually operate in production. This requires a full audit of data flows, API dependencies, batch processes, third-party integrations, security exposure, and workflows that must remain 100% live, including authentication, balance checks, payments, card transactions, and customer support operations.
Working on the Caribbean Bank case, we began by identifying which processes could not tolerate interruption under any circumstances and which capabilities could be safely isolated and modernized. This separation made it possible to introduce new functionality without destabilizing the core, laying the foundation for modern banking technology solutions that evolve around legacy systems rather than replace them abruptly.
A proper discovery phase in banking modernization includes:
• Architecture and dependency mapping: services, databases, message queues, tightly coupled modules, and high-risk integration points.
• API and integration inventory: active and undocumented interfaces, third-party connections, manual workarounds, and fragile contracts.
• Data flow analysis: data origins, transformations, synchronization points, duplication, and transaction-critical datasets.
• Security and compliance baseline: identity and access controls, encryption, audit logging, regulatory exposure, and external access risks.
• Operational constraints: peak loads, release windows, historical incidents, SLAs, and recovery expectations.
• Risk classification: components suitable for phased modernization versus those requiring parallel run or isolation.
The outcome of this step is a clear migration roadmap with defined boundaries, dependencies, risks, and sequencing. It determines what can be modernized first, how changes are validated, and under which conditions traffic can be safely shifted.
Step 2. Establish modernization governance to control risk and delivery
Legacy banking modernization without downtime requires more than technical execution. It needs a clear governance model that aligns business priorities, technology decisions, compliance requirements, and delivery cadence. Without this structure, modernization efforts fragment into isolated initiatives, increasing operational and regulatory risk.
In the Caribbean Bank project, limited in-house engineering capacity made governance especially critical. Early in the engagement, we defined how decisions would be made, who would own which risks, and how release approvals would be managed. This prevented delays caused by unclear ownership and ensured modernization progressed without disrupting live banking services.
Effective modernization governance includes:
• Defined decision roles: executive sponsor, product owners, architecture leads, compliance, and risk representatives.
• Release authority and escalation paths: who approves production changes, who can halt a release, and under what conditions rollback is triggered.
• Change control aligned with delivery: modernization work planned in increments, each with clear acceptance criteria tied to uptime, performance, and compliance.
• Embedded risk and compliance review: regulatory requirements addressed continuously, not after development is complete.
• Business participation in prioritization: modernization initiatives ranked by customer impact, risk reduction, and operational value—not technical convenience.
For Caribbean Bank, this structure ensured that integration with Visa and updates to digital banking interfaces progressed in parallel, without competing for attention or creating unmanaged dependencies. Business stakeholders remained directly involved in prioritization, while technical teams executed against clearly defined constraints.
This step ensures predictable execution by turning modernization into a coordinated program with measurable outcomes, controlled risk, and consistent progress. Governance establishes the discipline needed to modernize legacy platforms while maintaining continuous service.
Step 3. Start modernization at the edges before touching the core
Successful banking modernization often starts with peripheral systems rather than the core system itself. Banks achieve safer, faster results by upgrading these components—systems that connect to the core but do not impact its transactional stability. These systems offer an ideal environment for testing architecture choices, delivery methods, and integration patterns without risking the core systems.
In the Caribbean Bank case, modernization started outside the core by introducing new card transaction capabilities through a dedicated integration layer. This approach allowed the bank to expand digital services while keeping core banking operations unchanged, enabling legacy banking application modernization without disrupting critical systems.
Peripheral systems well-suited for early modernization include:
• card and payment processing layers,
• fraud detection and monitoring tools,
• customer-facing digital channels (web and mobile),
• CRM and customer data enrichment services,
• reporting, analytics, and notification services.
Modernizing these components first delivers immediate business value and creates a controlled proving ground for architecture and deployment practices.
The technical foundation for this step is a microservices architecture in banking, enabling new services to be developed, deployed, and scaled independently. APIs act as stable contracts between legacy systems and new components, ensuring that existing business logic remains intact while new functionality evolves around it.
Key implementation principles at this stage include:
• isolating new capabilities behind API gateways,
• avoiding direct database coupling with legacy systems,
• implementing centralized logging, monitoring, and tracing from day one,
• validating service behavior under real transaction volumes,
• enforcing backward compatibility to protect dependent systems.
For Caribbean Bank, this edge-first strategy enabled faster release cycles and reduced coordination overhead. New services could be tested, validated, and rolled out incrementally, while legacy systems continued to operate without modification.
The outcome of this step is early momentum with controlled risk. Banks gain visible improvements in customer experience and operational flexibility, while establishing the technical and organizational patterns required for deeper modernization later. This creates confidence across teams and sets the stage for safe, phased evolution of the core platform.
Step 4. Introduce a parallel run to decouple change from risk
Once new services are live at the edges, the next objective is to remove dependency on single-system behavior. This is achieved through a parallel run strategy—operating legacy and modern components simultaneously until the new path proves stable under real production conditions.
In the Caribbean Bank project, this approach was essential. Card transaction flows, authorization logic, and payment processing were introduced through a new service layer, while the legacy core continued to handle existing operations. Both environments ran in parallel, allowing teams to compare outputs, monitor behavior, and validate results before routing full traffic to the modernized components. This is a critical phase of banking infrastructure modernization, where reliability matters more than speed.
Parallel run strategies typically include:
• active–passive mode: legacy systems remain the system of record, while new services receive mirrored data for validation,
• active–active mode: both systems process transactions concurrently, with reconciliation and comparison layers ensuring consistency,
• feature-based routing: only specific user groups, regions, or transaction types are routed through the new stack,
• traffic gating: automated thresholds that block promotion if error rates, latency, or reconciliation metrics exceed limits.
To support this safely, banks should also implement:
• real-time data synchronization between systems,strict idempotency rules for financial transactions,
• detailed audit logs for every operation across both paths,
• rollback mechanisms that can shift traffic back instantly.
The outcome of this step is operational confidence. By proving new components under real load, while legacy systems remain fully functional, banks reduce migration anxiety, avoid irreversible mistakes, and create a controlled path toward deeper modernization without service downtime.
Step 5. Plan and execute data migration as a controlled, verifiable process
Data migration is the riskiest phase of banking shifts. Errors can disrupt functions, cause reconciliation problems, regulatory risks, and trust issues. It should be treated as engineering, not just a technical task.
In the Caribbean Bank project, data handling was central to enabling card transactions and payment processing without destabilizing existing operations. Rather than attempting a single cutover, data flows were carefully mapped, validated, and introduced in stages to support a financial services legacy system upgrade, where accuracy and auditability were non-negotiable.
A safe data migration strategy includes:
• Comprehensive data inventory: identifying all data sources, ownership, formats, and dependencies across legacy and modern components.
• Explicit data mapping: defining how each data element is transformed, stored, and consumed in the new architecture.
• Data quality checks: removing duplicates, correcting inconsistencies, and standardizing formats before migration begins.
• Incremental migration: moving data in controlled batches instead of a single bulk transfer.
• Dual validation: verifying results at both technical (schemas, counts, checksums) and business levels (balances, transactions, reporting outputs).
During the Caribbean Bank modernization, no migrated dataset was considered production-ready until it passed reconciliation checks against the legacy system. This allowed teams to identify discrepancies early and correct them without impacting customers or creating regulatory risk.
Security and compliance are embedded throughout this step:
• encryption for data at rest and in transit,
• controlled access and role-based permissions,
• full audit trails for every migration activity,
• repeatable test migrations to validate assumptions.
The outcome of this step is data continuity with zero disruption. Banks gain confidence that modernized services operate on accurate, trusted data while legacy systems remain stable. This foundation is critical before expanding modernization deeper into core processes or scaling new services across regions and customer segments.
Step 6. Prepare the platform for cloud-ready operation and scalable delivery
Downtime-free modernization requires systems that can scale, deploy, and recover predictably. Even if a bank does not move its core to the cloud immediately, newly modernized components must be cloud-ready by design. This prevents future rework and allows gradual infrastructure evolution without disrupting live services.
While working on the Caribbean Bank case, we designed the modernization layer to enable new services to operate independently of the underlying infrastructure. Containerization and automated provisioning enabled scaling of card-processing and digital-banking workloads as demand grew, while legacy systems continued to run unchanged. This approach laid a practical foundation for cloud migration for banking systems without forcing premature core relocation.
Cloud readiness at this stage focuses on capabilities:
• Containerized services: consistent runtime environments across development, testing, and production.
• Infrastructure as code: repeatable, auditable infrastructure changes with minimal manual intervention.
• Environment parity: development, staging, and production environments behave consistently.
• Horizontal scalability: the ability to scale individual services without affecting others.
• Automated recovery: predictable rollback and redeployment paths when issues occur.
For Caribbean Bank, these practices enabled faster releases and safer scaling across regions. New features could be deployed independently, validated under real load, and adjusted without coordinating large, high-risk infrastructure changes.
Security and compliance remain integral:
• secure configuration management across environments,
• controlled secrets handling and access policies,
• consistent logging and monitoring regardless of deployment location.
This step results in operational resilience, enabling banks to confidently deploy and scale services, handle traffic spikes, and prepare for future cloud adoption without downtime or lock-in. This readiness is crucial before expanding modernization or launching services in multiple markets.
Step 7. Embed security, compliance, and auditability into every modernization layer
In banking, security and compliance cannot be treated as a final checkpoint. They must be built directly into architecture, delivery pipelines, and operational processes. Downtime-free modernization fails when controls are added after functionality is implemented, creating release delays, emergency fixes, and regulatory exposure.
In the Caribbean Bank case, compliance requirements were a primary constraint from day one. Card processing and payment flows had to meet PCI DSS standards while operating alongside legacy systems. Instead of retrofitting controls later, security and governance were embedded in the modernization layer itself, ensuring new services could scale without creating compliance risk. This approach reflects how mature banking platform modernization services are delivered in regulated environments.
Key security and compliance elements at this stage include:
• Identity and access management: role-based access, least-privilege policies, and controlled service-to-service authentication.
• End-to-end encryption: data encrypted both at rest and in transit, including inter-service communication.
• Audit logging by design: immutable logs for transactions, configuration changes, and access events.
• Continuous compliance validation: automated checks aligned with regulatory and internal policies.
• Operational monitoring: real-time visibility into security signals, anomalies, and performance degradation.
For Caribbean Bank, this meant every transaction processed through the new integration layer was traceable, auditable, and protected without relying on manual controls. Security reviews did not block releases because controls were already part of the delivery process.
This step also establishes long-term governance:
• standardized security patterns reusable across services,
• consistent compliance posture as new capabilities are added,
• reduced risk of fines, incidents, and emergency remediation.
The outcome is scalable trust. Banks gain the confidence to modernize faster because every new component inherits the same security and compliance guarantees as the rest of the platform, without increasing operational friction or risk of downtime.
Step 8. Train teams and operationalize change to sustain modernization
Even the most robust technical architecture will fail if teams are not prepared to operate it. Downtime-free modernization depends on people understanding how the new system works, why changes were made, and how to respond when something goes wrong. This step ensures modernization becomes an operational capability rather than a one-off project.
In the Caribbean Bank project, new services, deployment models, and monitoring practices required changes in day-to-day operations. Teams responsible for support, releases, and incident response were gradually introduced to the new architecture while legacy systems remained active. This overlap allowed staff to learn without pressure and reduced the risk of operational errors during live usage.
Effective enablement at this stage includes:
• Targeted training by role: operations, support, security, product, and compliance teams focus only on what affects their responsibilities.
• Runbooks and playbooks: clear procedures for incident response, rollback, escalation, and reconciliation.
• Shadow operations: teams operate new services in parallel with legacy ones before assuming full responsibility.
• Release readiness checks: ensuring teams and systems are prepared before scaling traffic.
• Post-release feedback loops: capturing issues early and feeding them back into delivery and governance processes.
For Caribbean Bank, this approach ensured that modernization did not introduce operational fragility. Support teams could troubleshoot new transaction flows, security teams understood audit paths, and release managers had confidence in rollback mechanisms—without depending on ad hoc knowledge or external intervention.
This step also addresses organizational resistance. When teams see measurable improvements, faster releases, fewer incidents, and clearer visibility, they shift from defending legacy processes to supporting ongoing change.
The outcome is sustainable modernization. Teams can not only operate new services, but also confidently deploy, monitor, and support them in real production environments. This operational readiness is what ultimately enables a banking system upgrade without downtime, where modernization continues safely over time, without service interruptions, regulatory breaches, or loss of customer trust.
While architecture and delivery patterns are critical, user experience often determines whether modernization succeeds in practice. We explore this topic in “How to Redesign Legacy Financial Apps for Better UX and Staff Productivity.”
Strategic Takeaways
Modernizing legacy banking systems without service downtime is an operational necessity. Banks that succeed approach modernization as a controlled, phased transformation, combining strong governance, incremental architecture changes, parallel execution, and embedded security.
The Caribbean Bank case demonstrates that value can be delivered early without destabilizing core operations when modernization is guided by practical experience and disciplined execution.
With the right banking software development services, financial institutions can evolve critical platforms, reduce long-term risk, and accelerate innovation while maintaining continuous service availability and regulatory confidence.

Explore a pragmatic modernization approach that upgrades core banking systems while preserving uptime, customer trust, and regulatory stability.
Challenges banks face when they modernize legacy banking systems
Banks face increasing pressure to modernize, yet execution remains complex due to long-standing reliance on outdated core platforms. These systems were not designed for real-time processing, frequent regulatory change, or modern digital channels, making core banking system modernization a high-risk, multi-year effort rather than a simple technology upgrade.
1. Limited compatibility with modern technologies. Legacy cores integrate poorly with cloud services, fintech platforms, and real-time digital products. Even when integrations are feasible, they often lead to fragmented architectures and inconsistent customer experiences, slowing down digital transformation in banking.
2. Excessive complexity and hard-coded logic. Decades of customization have turned many core systems into tightly coupled, difficult-to-change environments. Minor updates can trigger cascading issues, while outdated documentation and a shrinking pool of skilled experts increase the risk of disruption during legacy system modernization in banking.
3. Regulatory and compliance pressure. Banking regulations evolve rapidly, yet legacy platforms lack the flexibility and automation needed to adapt efficiently. Manual controls and fragmented data increase the risk of non-compliance, fines, and operational exposure during modernization.
4. Cost inefficiency and scalability limits. Maintaining legacy cores consumes up to 78% of IT budgets, leaving little room for innovation. At the same time, these systems struggle to scale across growing product portfolios and digital channels, increasing performance and outage risks. Banks that modernize report cost reductions of up to 25% and operational risk reduction of up to 30%, highlighting the long-term impact of outdated platforms.
5. Execution and sustainability risk. Even successful transformations are hard to sustain. Many initiatives fail to deliver lasting value due to weak governance, fragmented execution, and organizational resistance, reinforcing the need for a controlled, phased modernization approach.

For more information on the role of AI in financial services, read AI Solutions in Capital Markets: Trends, Opportunities, and Challenges.
How Computools can help you with legacy banking system modernization
Computools helps financial institutions approach legacy banking system modernization as a controlled, business-driven transformation rather than a disruptive core replacement. The focus is on maintaining service continuity, strengthening regulatory alignment, and delivering measurable operational improvements while legacy platforms remain fully operational.
We deliver custom finance software for banks, fintech companies, insurers, and investment firms, combining financial domain expertise with modern engineering practices to modernize complex banking environments safely and predictably.
A representative example is the Caribbean Bank project. Operating across 17 countries, the bank needed to expand digital banking capabilities and introduce card processing without risking service disruption or regulatory exposure. Instead of replacing the core platform, Computools designed a microservices-based integration layer that enabled secure Visa connectivity, transaction authorization, and incremental feature rollout.
This approach allowed modernization to progress in parallel with existing systems, resulting in zero downtime, stronger PCI DSS compliance, improved scalability, and a 12% increase in market share among younger customers.
By applying phased architectural changes, decoupled integrations, and parallel system operations, Computools enables banks to evolve legacy platforms without disrupting day-to-day operations or customer-facing services. The result is a modernization path that reduces long-term operational risk, lowers maintenance costs, and restores confidence in launching new banking capabilities.
To discuss your legacy banking system modernization initiative, contact our team at info@computools.com.
For a broader market perspective, see our curated overview of Top 25 Fintech Software Development Companies in 2025, highlighting teams with proven experience in regulated, large-scale financial systems.
Computools
Software Solutions
Computools is a digital consulting and software development company that delivers innovative solutions to help businesses unlock tomorrow.








“Computools was selected through an RFP process. They were shortlisted and selected from between 5 other suppliers. Computools has worked thoroughly and timely to solve all security issues and launch as agreed. Their expertise is impressive.”