Financial and retail organizations that process cash and card transactions face enormous risks if their systems fail to comply with PCI DSS standards. Data breaches, fraud, and multimillion-dollar losses frequently result from weak payment security.
In 2023, just 14.3% of organizations were fully PCI-compliant, revealing major security gaps. The average retail data breach cost is $3.28 million, emphasizing the financial importance of payment security. To prevent these risks and ensure resilience, businesses invest in PCI-compliant cash-handling software that safeguards sensitive transactions and builds customer trust.
Computools supports these initiatives; we have worked with over 20 retail and 20+ financial companies delivering retail software development services and banking software development, as well as solutions that ensure PCI compliance in the financial industry. Standards and security were critical for all of them, which is an inalienable condition for market participation.
As a company certified according to ISO 9001 and ISO 27001 standards, we know how to implement all these points, so we consider the case of our client as an example.
Here is how we built PCI-compliant cash-handling software for a global leader
With hands-on experience in PCI compliant app development, we partnered with a global leader in intelligent cash-handling solutions, securing over $4 billion daily across banking, retail, and the leisure industry.
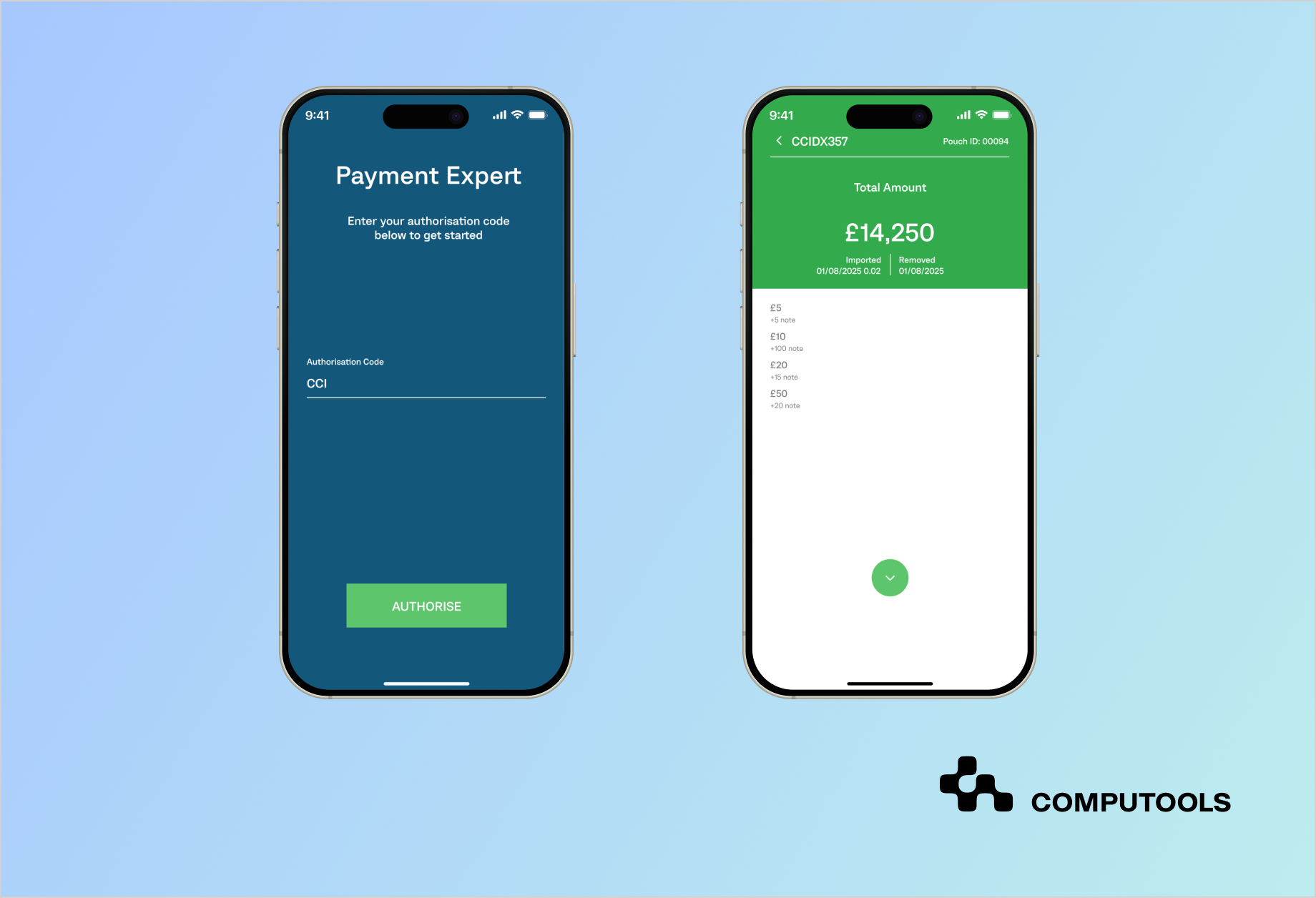
Their products enhance security, optimize processes, and reduce shrinkage (losses from theft or errors). We implemented the CCI Assistant project for this client, modernizing an outdated mobile app and transforming it into a secure, user-friendly, and efficient solution.
This example highlights why payment security is such a critical issue globally. In the first half of 2023 alone, the EU and EEA reported fraud losses exceeding €4.3 billion, while global e-commerce fraud rose to $48 billion, nearly 3% of worldwide online revenue.
These figures show that secure cash handling solutions for financial retail operations and secure payment processing are not optional but fundamental to protecting revenue and customer trust.
How to build PCI-compliant cash-handling software
PCI DSS compliance is an ongoing process that requires a comprehensive approach, covering both technology and internal processes. Compliance is about system architecture, data protection, and a strong culture of security within the company, all essential aspects when considering how to build PCI-compliant cash-handling software that is both secure and scalable.
Step 1: Architecture and network.
As part of PCI compliant app development, the first step is a properly configured infrastructure. This means creating strict network segmentation so that systems dealing with cardholder data are entirely isolated from testing or non-production environments. Separating test and production eliminates the risk of exposing real card data during development or QA processes.
On top of that, firewalls and intrusion detection/prevention systems form the outer security perimeter. Properly configured firewalls filter both inbound and outbound traffic, blocking unauthorized access while allowing legitimate payment transactions to flow smoothly. PCI DSS also recommends avoiding vendor default settings and documenting firewall rules for regular review.
In practice, this step often includes:
• isolating the cardholder data environment (CDE) from the corporate network;
• using VPNs or secure tunnels for remote administration;
• regularly testing firewall rules against penetration attempts.
For example, Computools began with a complete audit of the client’s infrastructure in the CCI Assistant modernization project. Test and production were separated into independent environments, ensuring no overlap of live transaction data.
This foundational work aligned with enterprise-grade PCI DSS compliant payment systems and laid the groundwork for building secure retail software solutions that made subsequent data protection, access control, and monitoring far more effective.
Step 2: Data security
Protecting sensitive financial data lies at the core of PCI DSS. According to the PCI DSS requirements, cardholder information such as the Primary Account Number (PAN) or CVV must never be stored in plain text. Instead, businesses are expected to implement strong encryption, tokenization, and retention policies that ensure sensitive data is either anonymized or securely destroyed once it is no longer needed.
In practice, this means:
• Encryption in storage and transit. All cardholder data must be encrypted when saved in databases or transmitted across networks, using modern protocols like TLS 1.2+ or P2PE (Point-to-Point Encryption).
• Tokenization. Real card numbers are replaced by tokens that can only be mapped back through secure vaults, minimizing the risk even if systems are compromised.
• Data minimization. The safest data is the data you don’t keep. Companies should limit storage strictly to what is operationally necessary and define clear deletion policies.
Computools implemented secure document handling through libraries like iTextSharp and SQLite ORM during the CCI Assistant project. These tools ensured that financial data never appeared in raw form, while encrypted storage and transmission protected it end-to-end.
As a result, the client’s new system aligned with PCI DSS technically and operationally, reducing exposure risks and building customer trust.
Step 3: Access control
Strong access management is one of the cornerstones of PCI compliant application development. Even the most advanced encryption can be undermined if unauthorized users access systems.
That is why PCI DSS requires companies to implement robust cybersecurity solutions for identity and access management.
Key practices include:
• Multi-Factor Authentication (MFA). Cashiers, managers, and administrators must log in using at least two verification factors (password + token, biometric, or SMS code). This dramatically reduces the risk of compromised credentials being misused.
• Unique user IDs. Every employee, contractor, or third-party provider must have a dedicated ID so their actions can be traced back individually. Shared accounts are strictly prohibited.
• Granular access rights. Permissions should follow the “least privilege” principle, giving users only the access necessary for their role.
• Detailed logging and monitoring. Comprehensive audit trails ensure full visibility of who accessed cardholder data, when, and for what purpose.
In the CCI Assistant project, Computools integrated Passport.js as an authentication framework. This allowed flexible configuration of access policies for different user groups while keeping logs centralized for compliance and audit purposes.
Such layered access control helped meet PCI DSS rules and strengthened the client’s internal governance, reducing insider threats and ensuring long-term resilience.

Step 4: Monitoring and testing
The PCI compliance checklist requires regular vulnerability scans, penetration testing, and transaction log monitoring. This proactive approach helps detect risks before attackers exploit them.
In practice, monitoring is more than a box-ticking exercise. Companies need to establish continuous logging of all activities within the cardholder data environment (CDE), with alerts for anomalies such as unusual transaction patterns, repeated failed login attempts, or unauthorized access to sensitive systems. Advanced SIEM (Security Information and Event Management) tools are often deployed to correlate events and flag potential threats in real time.
For modern enterprise payment software, penetration testing is essential as it simulates real-world attacks. Quarterly vulnerability scans combined with annual penetration tests help identify weaknesses in applications, POS systems, and connected infrastructure before hackers can take advantage of them. This practice also ensures alignment with international audit expectations for businesses operating across multiple regions.
In the CCI Assistant project, Computools implemented dashboards to track cash flow and card transactions in real time. These dashboards allowed managers to maintain operational oversight and integrated anomaly detection algorithms to flag suspicious operations automatically. This proactive setup turned monitoring into a business advantage, boosting security and efficiency.
Step 5: DevSecOps
In modern software delivery, security cannot be an afterthought; it must be built from day one. That’s why PCI compliant app development goes hand in hand with the DevSecOps approach, where development, security, and operations are fully integrated.
The core idea is “security by default.” Every stage of the software lifecycle, from the first line of code to deployment, includes automated checks and protective measures.
For example:
• Code reviews and static analysis detect vulnerabilities early, before they reach production.
• Automated security scans are embedded into CI/CD pipelines, so each new build is tested against compliance requirements.
• Infrastructure as Code (IaC) ensures consistent security configurations across environments, reducing misconfigurations that attackers could exploit.
• Continuous patching and updates prevent systems from becoming outdated or exposed to known vulnerabilities.
Computools used the Kanban methodology in the CCI Assistant project with two-week sprints, delivering new builds regularly. This iterative process allowed the team to incorporate security testing at every cycle, ensuring compliance was maintained without slowing delivery. The result was a PCI DSS-compliant product and a faster, more reliable development pipeline.
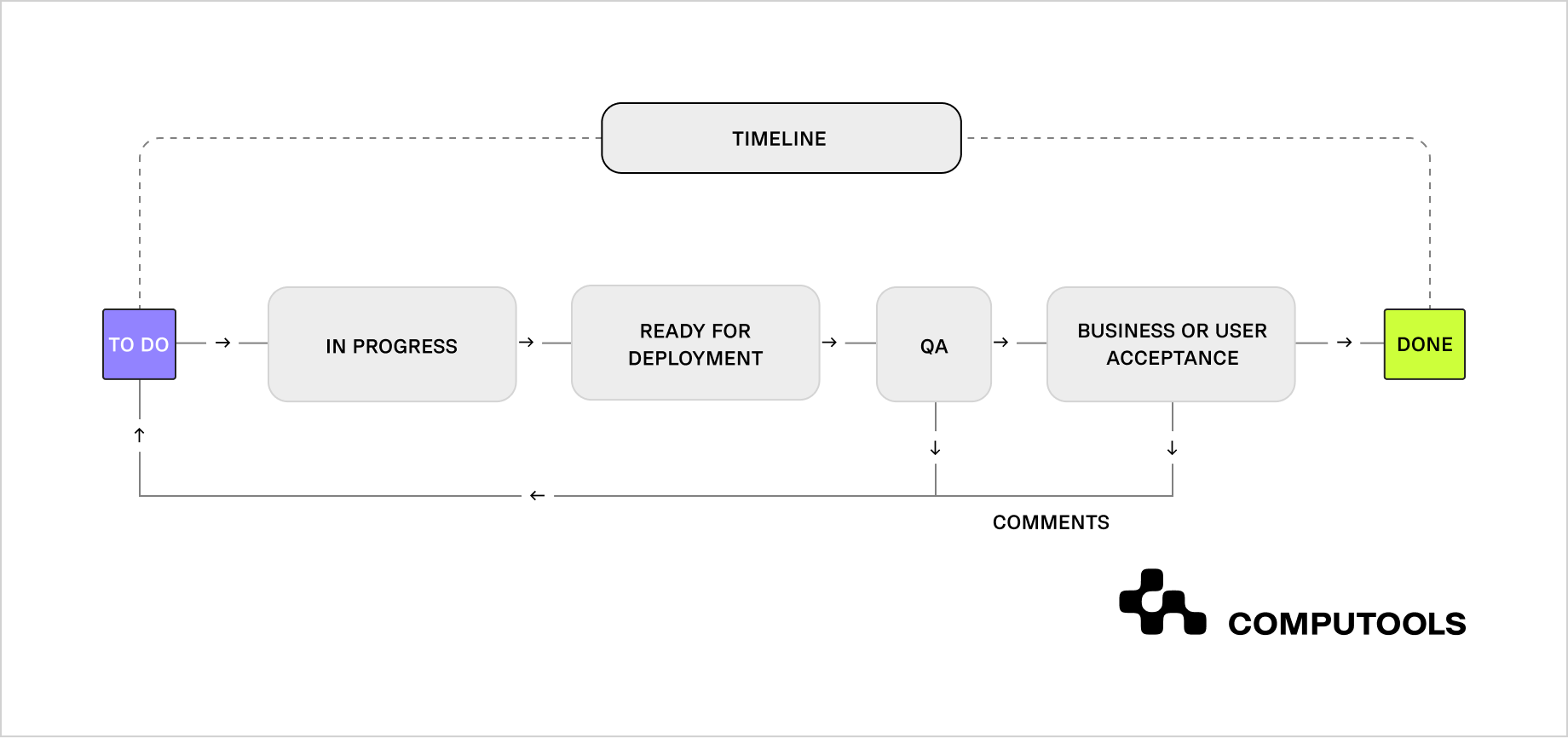
Key principles to follow
Building PCI-compliant cash-handling software involves more than merely fulfilling technical specifications; it also requires fostering a strong security culture.
These golden rules apply across finance, retail, and beyond:
1. Store only what is necessary. The safest data is the data you don’t keep. Limit cardholder data retention to the absolute minimum.
2. Encrypt everything in transit. From TLS protocols to P2PE (Point-to-Point Encryption), ensure card data is unreadable outside secure environments.
3. Keep systems up to date. Regular patches for POS terminals, servers, and antivirus tools close vulnerabilities before attackers can exploit them.
4. Control physical access: secure server rooms, payment terminals, and storage devices. PCI DSS also requires strict documentation of who can enter sensitive areas.
5. Log and test continuously. Activity logs and regular penetration tests aren’t just paperwork; they are active defenses against fraud and data leaks.
Together, these principles serve as the foundation for trust. They meet PCI DSS standards and make payment operations more resilient, efficient, and customer-focused.
The CCI Assistant case shows how legacy systems can be transformed into modern PCI compliant software that meets today’s security and usability standards.
By redesigning architecture and workflows, Computools delivered reliable cash handling software that reduced risks, improved efficiency, and strengthened customer trust. This example highlights how compliance and innovation together create long-term business value.

Cutting corners today creates risks tomorrow. Build PCI-compliant software that scales securely and earns lasting trust.
What are the consequences of not being PCI-compliant?
Failing to meet PCI compliance in the financial industry brings severe risks: loss of card processing rights, costly QSA audits, and liability for fraud. Real-world breaches confirm the danger, such as Neiman Marcus (4.6M accounts exposed), Next Level Apparel (phishing), and over 4,000 hacked Magento stores due to poor POS systems integration and patching.
Only robust financial operations software and the best practices for PCI-compliant software development for finance and retail can reduce vulnerabilities and maintain customer trust.
Data security goes beyond PCI DSS. For a broader perspective on how financial institutions structure and protect sensitive information, read our article on Data Governance in Fintech Software Development.
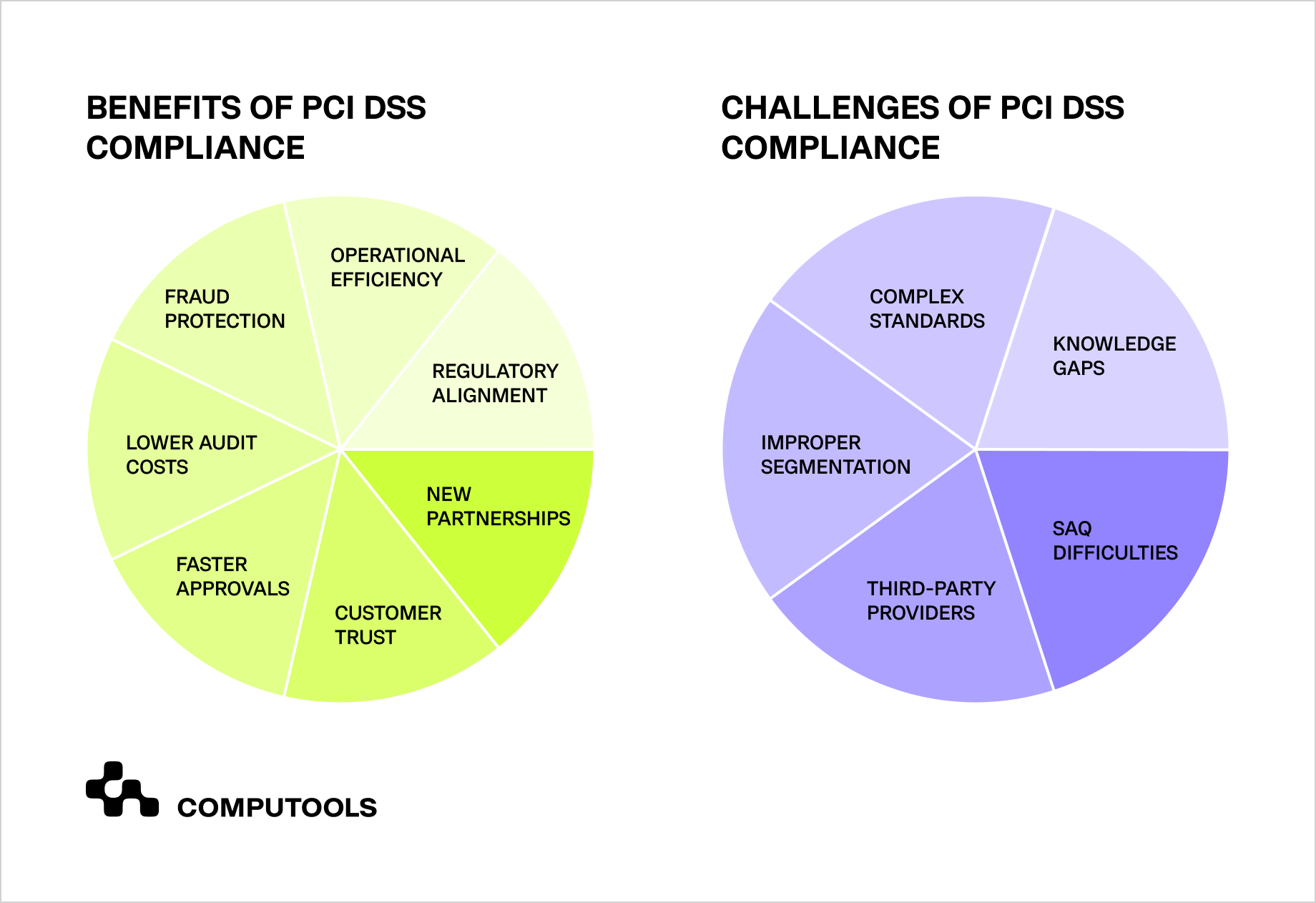
Challenges in PCI compliant app development
The road to secure app development with PCI compliance comes with multiple challenges, especially for businesses in financial and retail operations. Each sector faces unique complexity in ensuring compliance while maintaining smooth user experiences.
Financial Operations. Banks process millions of transactions daily, demanding strong encryption, tokenization, and core banking integration. Even minor software or encryption errors can expose data and cause costly failures in payment gateway compliance.
Retail Operations. For merchants, PCI compliance in retail means securing transactions across POS terminals, e-commerce checkouts, and cash-handling systems without slowing down customer service.
Legacy Systems. The CCI Assistant case shows this risk clearly: the old Windows Phone app was overloaded, slow, and inefficient. Computools delivered a modern, compliant solution that enhanced security, speed, and user experience by redesigning the architecture and UI.
Despite these barriers, PCI DSS reduces breach risks, builds trust, and aligns businesses with global standards protecting data while driving growth and competitiveness.
What are the benefits of PCI DSS compliance?
• Protection against card fraud and data leaks, ensuring sensitive card data remains secure.
• Reduced audit expenses and minimized penalties.
• Faster approvals from banks and payment systems, which streamlines operations.
• Stronger customer trust and loyalty thanks to a visible commitment to security.
• New partnership opportunities with processors and acquirers, opening doors to growth.
• Simplified alignment with other standards, such as GDPR or HIPAA.
More efficient operations through cash handling automation that reduces human error and improves accuracy.
Integrating PCI standards into secure retail software development ensures long-term resilience, compliance, and credibility in the market for retail and financial enterprises.
Our work on the CCI Assistant project is a clear example: Computools applied PCI compliant app development to modernize a legacy mobile solution. The result was improved performance, enhanced security, and complete alignment with PCI DSS standards, demonstrating how compliance directly leads to business growth and trust.
How to choose the right partner for PCI-compliant cash-handling software
Developing PCI-compliant solutions requires more than coding skills; it demands expertise in security, compliance, and industry-specific challenges. To ensure scalability and real-time monitoring, a reliable partner should combine digital transformation services with deep knowledge of financial regulations, retail operations, and advanced practices like IoT development.
With strong expertise in financial software development, Computools delivered a successful solution for the CCI Assistant case, modernizing a legacy system into a secure, efficient, and PCI-compliant mobile app.
Choosing the right vendor makes all the difference. Discover the Top Custom Retail Software Development Companies that help retailers improve efficiency and customer experience.
Conclusions
Strong compliance is not optional in today’s financial and retail sectors; it’s the foundation of secure growth. Companies that invest in financial software development aligned with PCI DSS protect sensitive transactions, prevent costly breaches, and build customer trust.
For retailers, implementing retail POS security software and modern POS software development ensures safe and seamless operations across omnichannel environments.
At the same time, building PCI-compliant mobile applications empowers businesses to combine innovation with uncompromised security, turning compliance into a competitive advantage.
Computools
Software Solutions
Computools is a digital consulting and software development company that delivers innovative solutions to help businesses unlock tomorrow.








“Computools was selected through an RFP process. They were shortlisted and selected from between 5 other suppliers. Computools has worked thoroughly and timely to solve all security issues and launch as agreed. Their expertise is impressive.”