Get in touch →
- Services
- Capabilities
- Industries
- Clients
- Approach
- About Us
- Blog
- EN
- Menu Item
- Get In Touch

As the leader of your organisation, you develop strategies that will help your business grow. You evaluate your resources, such as finances, human capital, and time. Your goal is to direct your efforts and investments to those areas that promise the greatest return.
You need to navigate between cost reduction and investing in areas that will drive future growth. It is important to evaluate both financial and non-financial aspects to develop a balanced and effective strategy. A ‘balanced strategy’ refers to a harmonious combination of different management elements, including investments in human resources, innovation and business sustainability. It also involves attention to corporate culture and customer satisfaction. Avoiding approaches that may lead to short-term gains at the expense of long-term sustainability, such as mass layoffs, is important. Instead, it is better to focus on identifying and avoiding potential challenges and problems that may arise in the course of implementing the strategy.
Your challenge is to determine which areas to invest in for future success. You factor in workforce issues like talent retention, diversity, equity, and inclusion, as well as environmental sustainability, when making decisions.
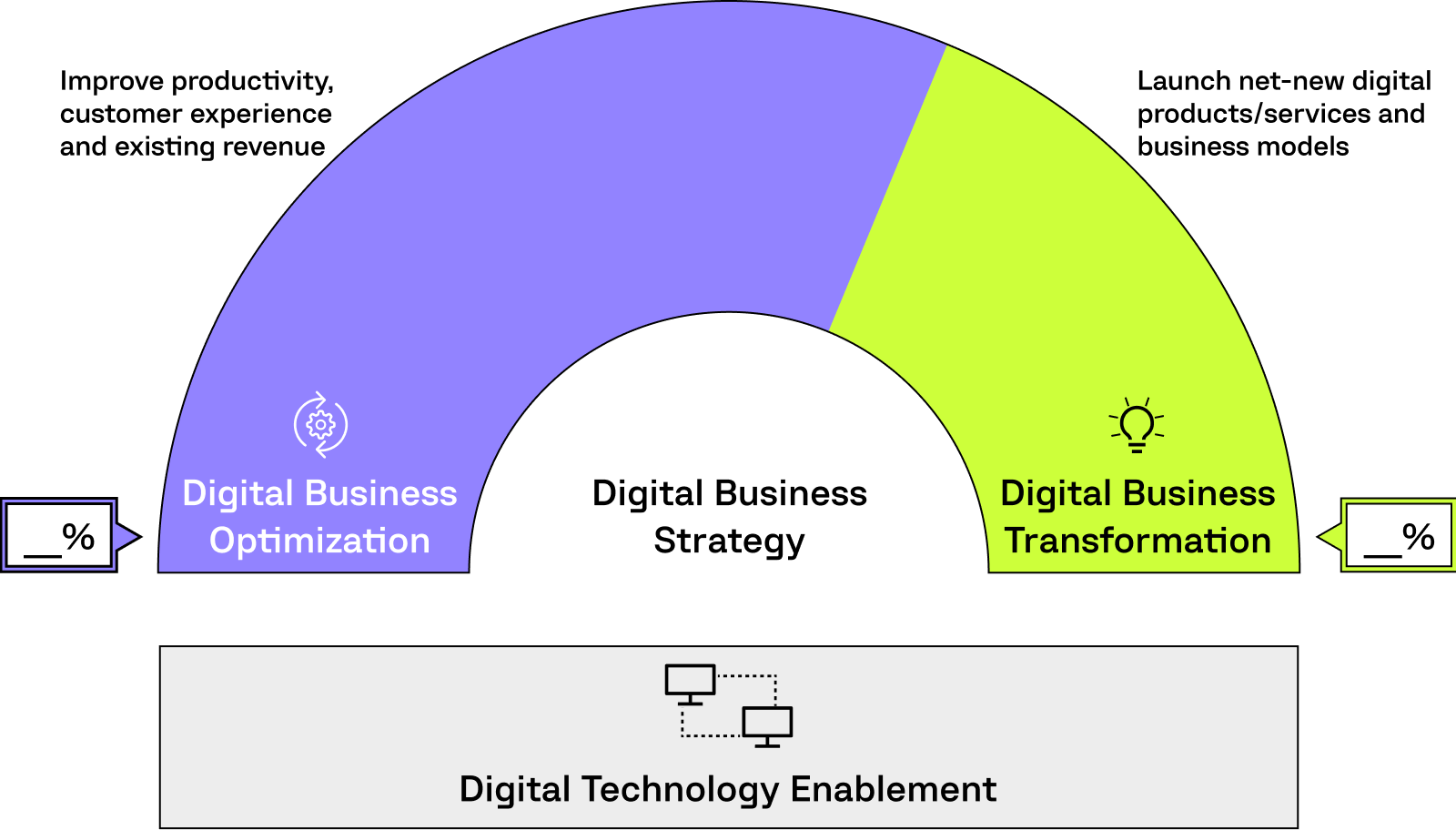
How to Start Digital Optimization:
At Computools, we apply the understanding of your business, values, and aspirations to craft strategies to achieve growth and efficiency via digital channels. In practice, we analyse your existing processes, identify areas for improvement, and offer practical solutions to achieve the results with technology. Our expertise encompasses a comprehensive suite of services designed to empower you to achieve exceptional results:
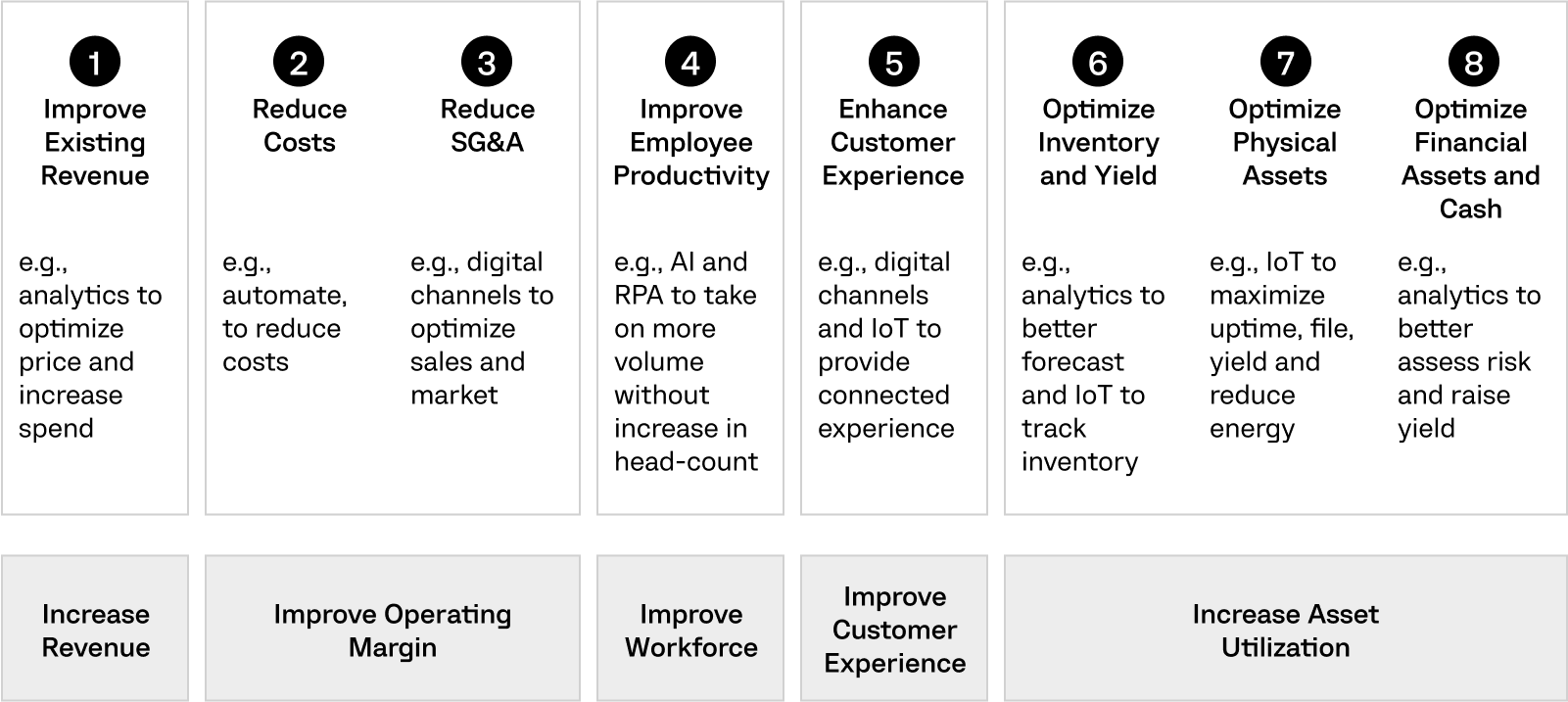
Our engineers leverage data and analytics to derive actionable insights and drive informed decision-making. They deploy predictive analytics models to forecast market trends and tailor strategies for sustainable growth.
We streamline your business processes through process automation. For example, we implement cloud-based collaboration tools to facilitate seamless communication and information sharing across departments. Furthermore, we can integrate Robotic process automation into routine, rule-based tasks to improve operational efficiency.
We offer modernisation in terms of upgrading and integrating systems to keep pace with evolving technologies and industry standards. Our engineers can transition your systems from legacy systems to modular architecture to achieve greater scalability and adaptability.
Computools is committed to environmental sustainability, offering services from creating tools for effective resource management to supply chain improvement. We strive to create a greener and healthier world through pollution prevention, resource management and active participation in the community.
As part of our service, we craft customer experience strategies and design seamless interactions across touchpoints. For example, our teams can apply user-centric design principles to optimise customer journeys and improve conversion rates.
We work with you to map out, analyse, and redesign your processes, eliminating bottlenecks and improving overall performance.
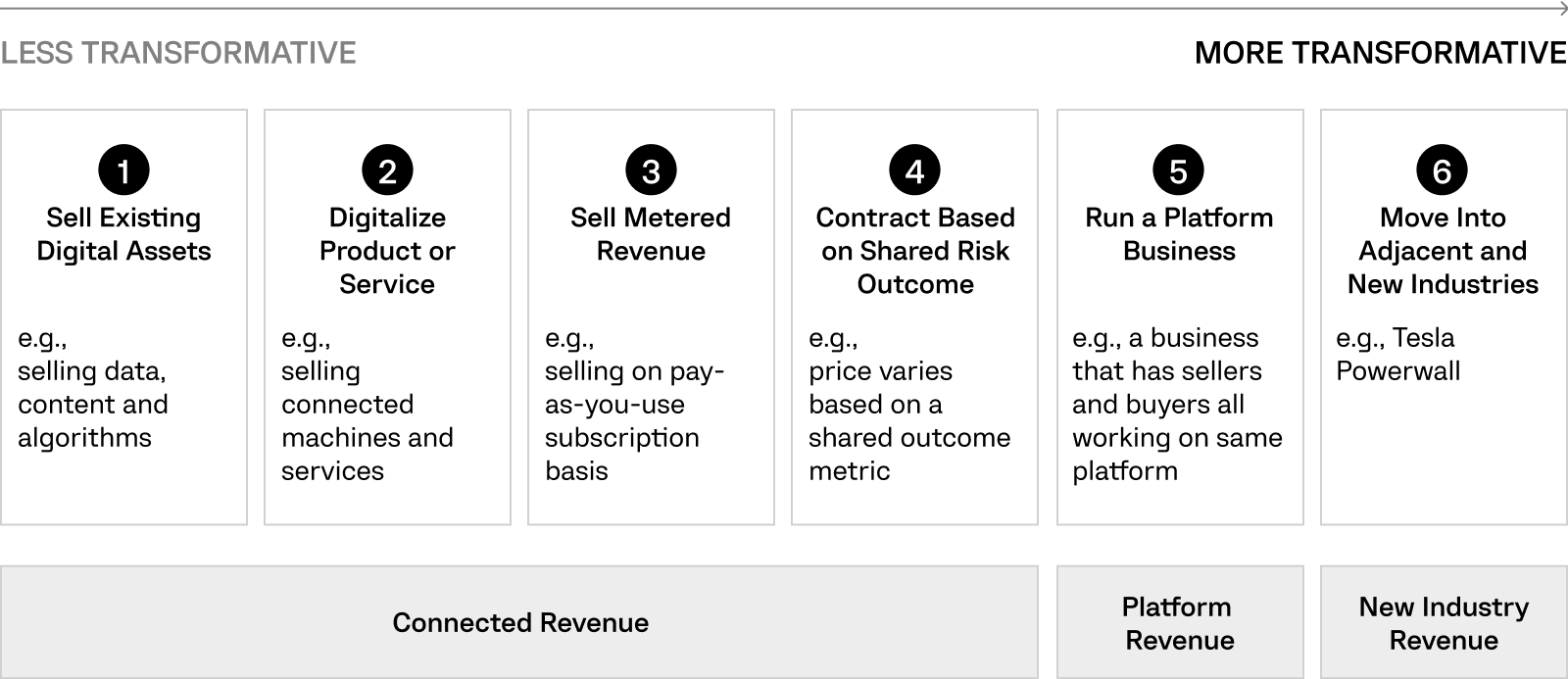
Computools delivers a powerful combination of platform technology, strategy, industry-specific and horizontal custom solutions to help you in your digital business optimization and transformation journey.
Develop a shared vision, establish sponsorship, communicate transformational messages, and create a blueprint for the desired end state. We set the stage for success by establishing a shared vision, securing leadership, communicating the transformation message, and crafting a clear roadmap.
Determine the order and priority of initiatives, taking into account your company’s capabilities and external factors. Establish program support, define governance frameworks, and delegate financial authority accordingly. Scrutinise every process, tool, and service. We help you streamline workflows, automate tasks, and consolidate resources. Every dollar saved is a dollar reinvested in your future.
Execute initiatives through iterative processes led by program officers and project leaders. Our program and project leaders deliver transformation initiatives guided by iterative cycles. This includes ongoing risk assessments, program oversight, and performance checks.
Take a fresh look at your technology stack and service providers. We help you with cloud migration, outsourcing, or switching vendors to increase efficiency and unlock potential cost savings. Sometimes change is the key to unlocking hidden potential.
We help you to develop technology, automate tedious tasks, and empower employees with self-service options. Streamlining operations releases resources for innovation and growth.
The savings you generate aren’t just about keeping the lights on. They are the fuel for your future. Invest in cutting-edge analytics, modernise your infrastructure, and adopt new organisational models to become more agile and competitive.